Filtering and sorting events in App Review
RocketCyber unveils an intuitive triage view interface that empowers users to effortlessly sort and filter through event data.
Accessing event triage
-
To begin, click Review in an app card.
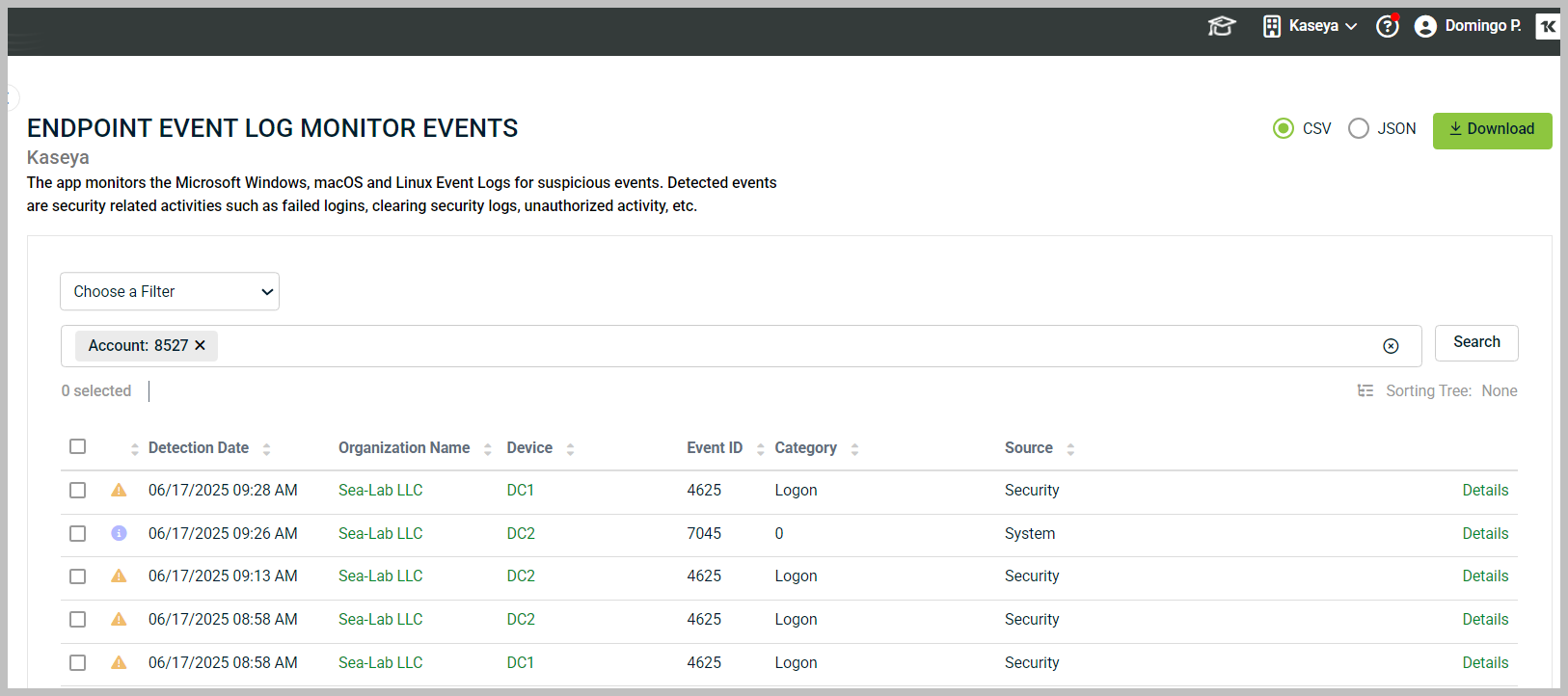
2. The event triage page is displayed. At the top of the page, you will notice a Search/Filter interface. The default filter for each page shows events relevant to the current account context. In the main area of the events triage page, known as the event grid, the associated data is displayed in rows and columns.
Each column in the event grid can be sorted by clicking the column header. You can sort by:
- Detection Date
- Organization Name
- Device
- Event ID
- Category
- Source
Filtering data
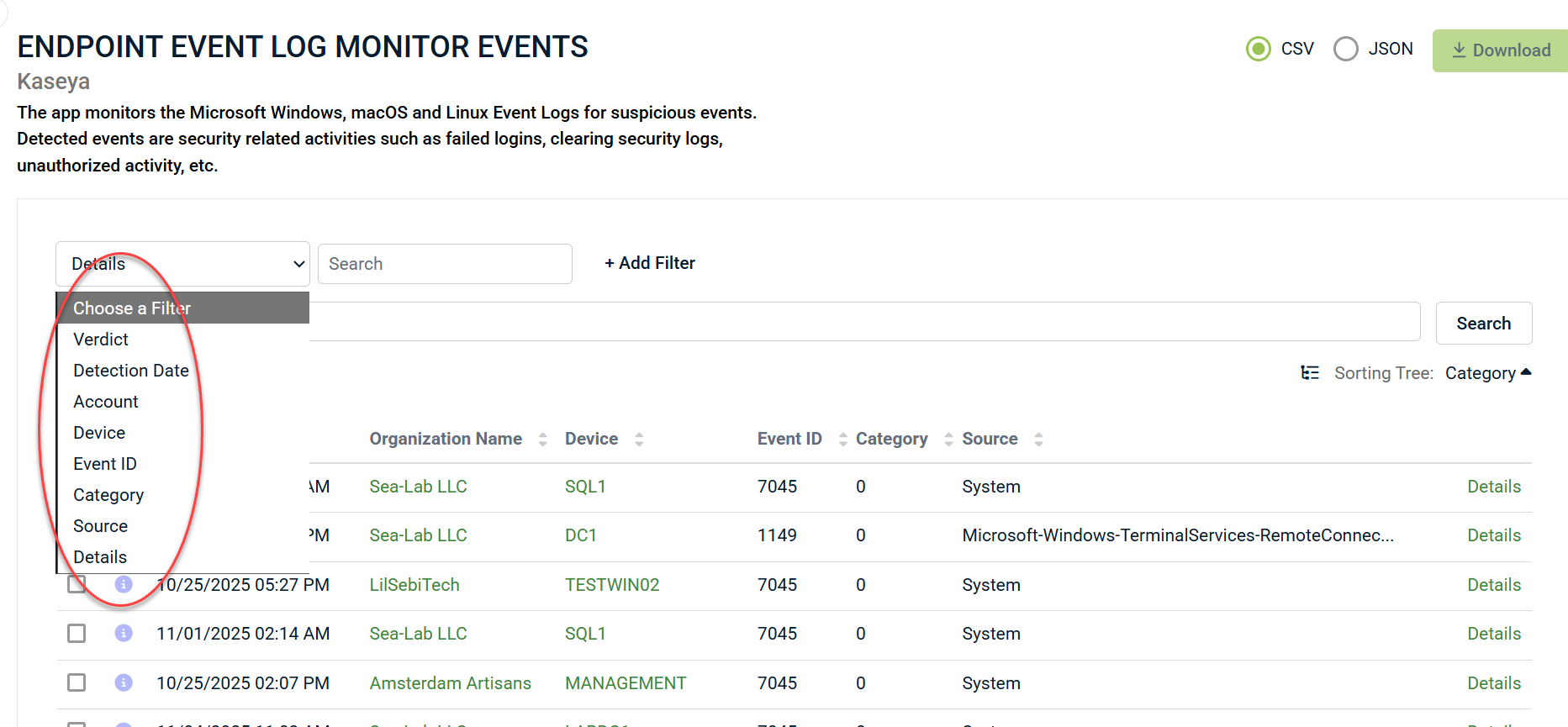
The process for searching and filtering data has been significantly improved with the Search/Filter interface. This interface provides quick ways to filter data based on the app being reviewed. For example, in the Endpoint Event Log Monitor App, the available default search fields are the following:
- Verdict
- Detection Date
- Account
- Device
- Event ID
- Category
- Source
- Details
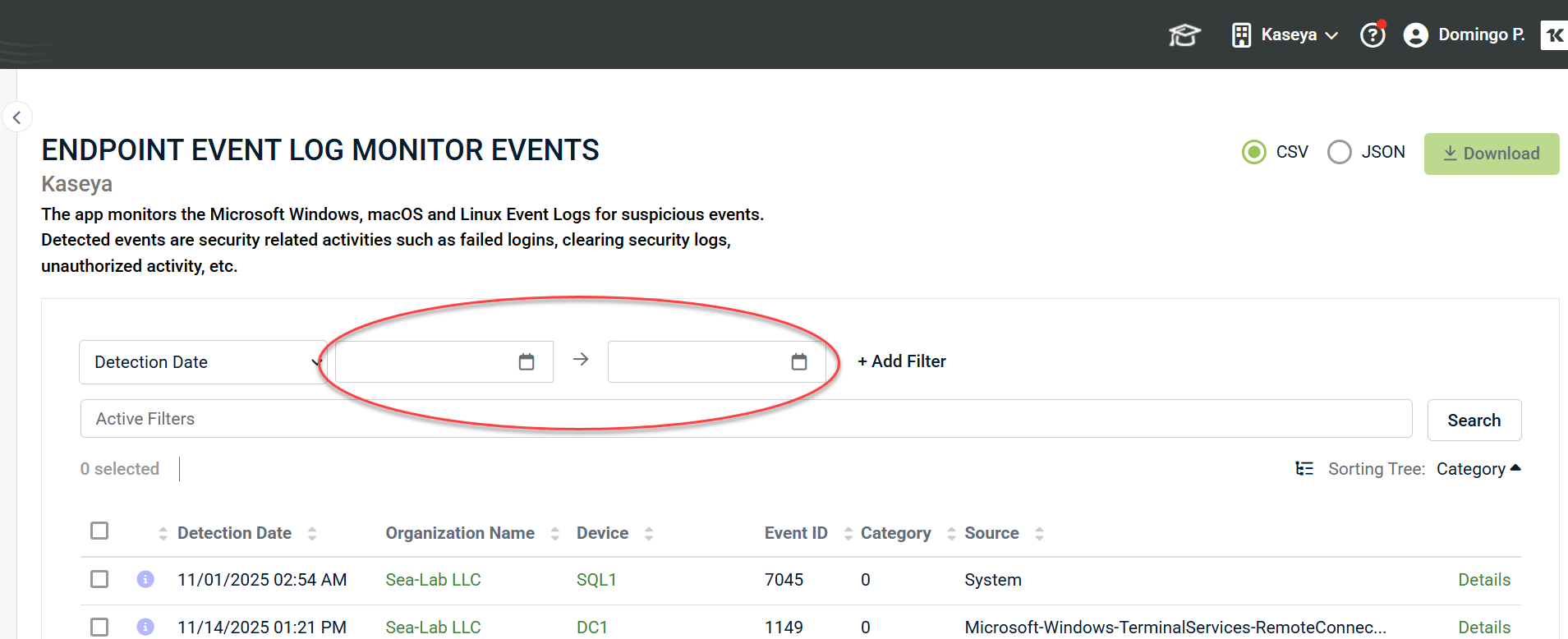
1. To illustrate filtering, let's select Detection Date from the filter list to find events that occurred during a specific timeframe.
NOTE Choosing a single Detection Date will return all events from that date through to the current date and time.
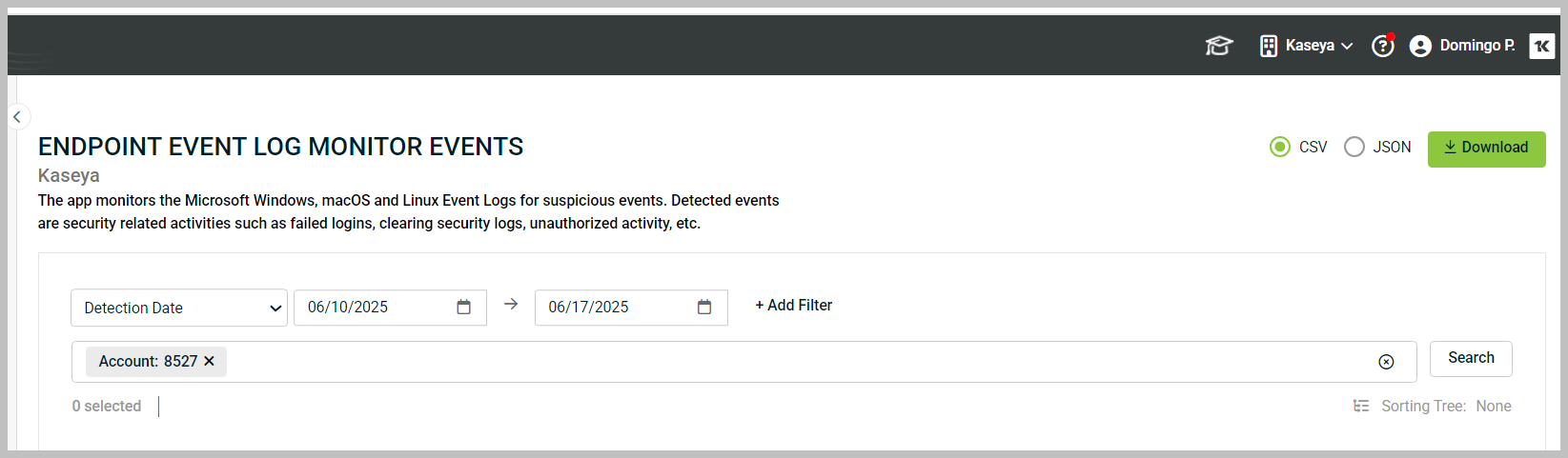
2. The Search interface will display fields for choosing a date range.
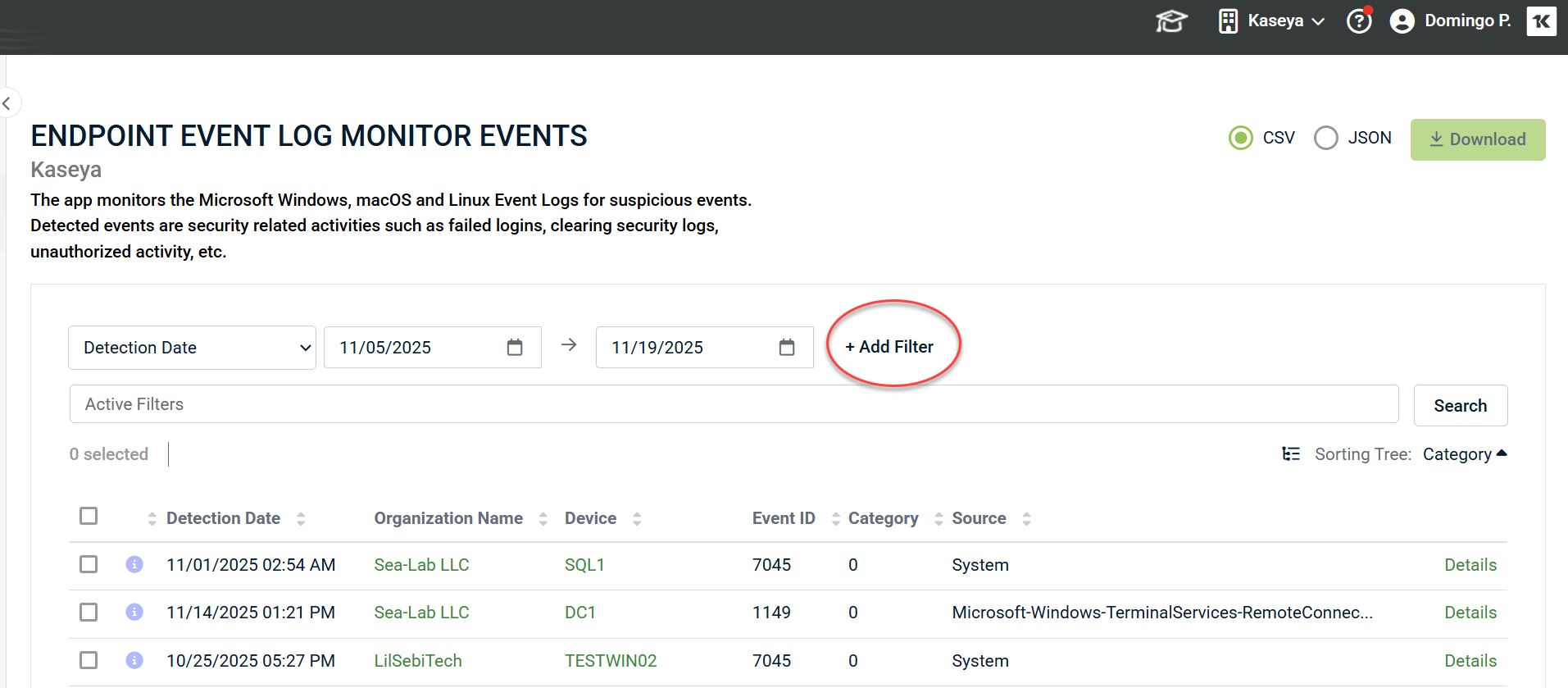
3. Once you have entered the date ranges, click + Add Filter.
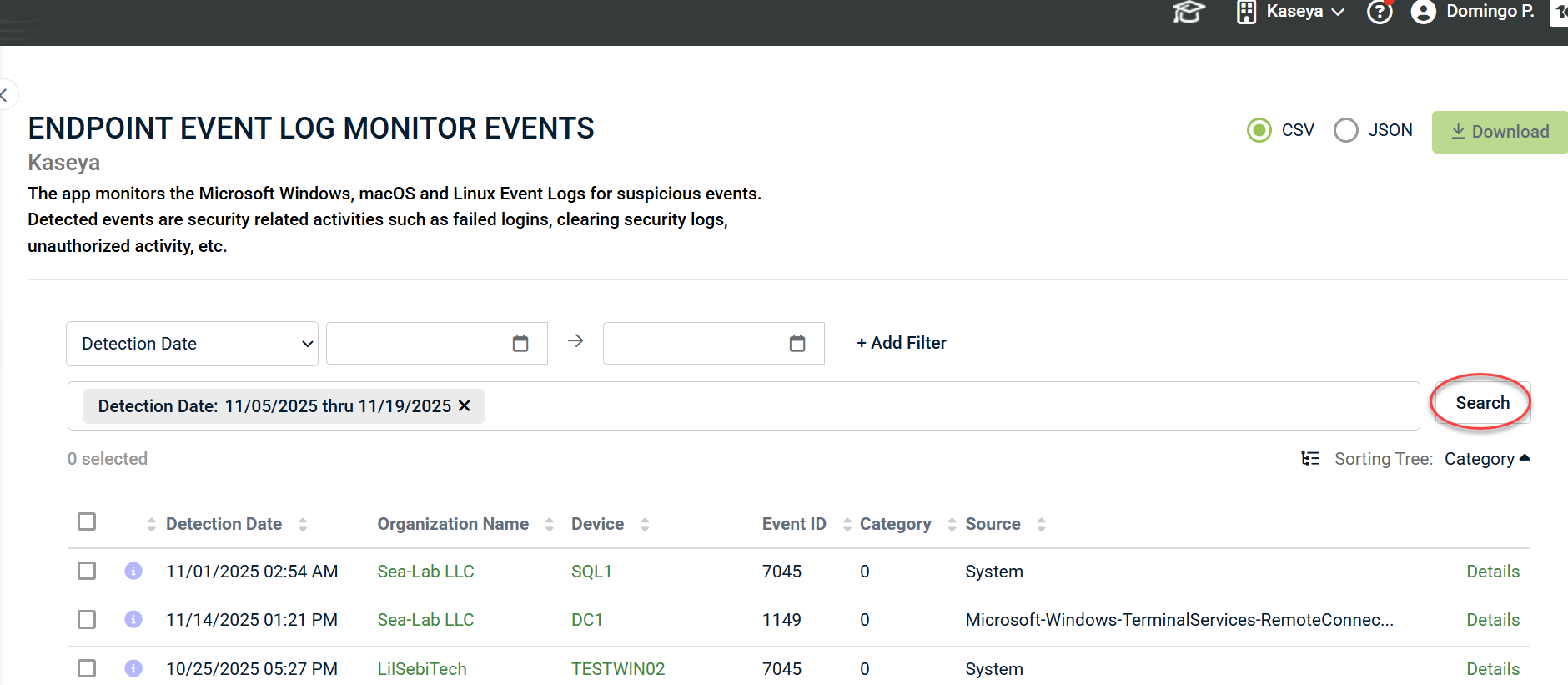
4. Then, click Search to display the desired results.
Filtering for multiple criteria
The search interface allows you to filter based on multiple criteria.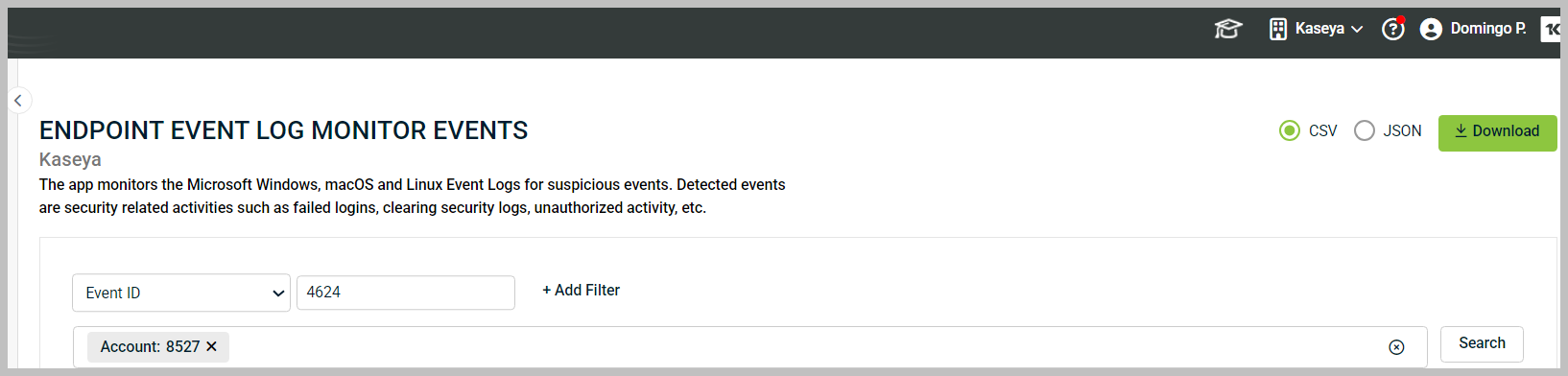
Building on the previous example of filtering by detection date, let's search for a specific event ID in that date range:
1. Select another search filter from the drop-down menu and click Event ID.
2. Enter the ID number 4624 in the ID value field, then click + Add Filter. You can add as many filters as necessary.
3. Once finished, click Search to display the desired results.
NOTE All search filters are combined using an AND operation to filter results.
In the previous example, results will only be displayed if the Detection Date is between 11/05/2025 AND 11/19/2025 AND the event id is 4624.
Filtering for details - Advanced
Events can be filtered by specific attributes found in the details of an event. To review these attributes, download the JSON from the console and analyze the JSON structure.
For Endpoint Event Log details, the structure may look like this:
{
"type": "EventLogMonitor",
"attributes":
{
"xml": "<Event xmlns='http://schemas.microsoft.com/win/2004/08/events/event'><System><Provider Name='Microsoft-Windows-Eventlog' Guid='{fc65ddd8-d6ef-4962-83d5-6e5cfe9ce148}'/><EventID>104</EventID><Version>0</Version><Level>4</Level><Task>104</Task><Opcode>0</Opcode><Keywords>0x8000000000000000</Keywords><TimeCreated SystemTime='2022-04-03T04:49:54.696269100Z'/><EventRecordID>1507515</EventRecordID><Correlation/><Execution ProcessID='980' ThreadID='992'/><Channel>System</Channel><Computer>Joe-User.rocketcyber.com</Computer><Security UserID='S-1-5-18'/></System><UserData><LogFileCleared xmlns='http://manifests.microsoft.com/win/2004/08/windows/eventlog'><SubjectUserName>SYSTEM</SubjectUserName><SubjectDomainName>NT AUTHORITY</SubjectDomainName><Channel>Windows PowerShell</Channel><BackupPath></BackupPath></LogFileCleared></UserData></Event>",
"opcode": "Info",
"message": "The Windows PowerShell log file was cleared.",
"version": 0,
"event_id": 104,
"log_name": "System",
"record_id": 1507515,
"telemetry":
{
"event_sent_to_cloud": 1648961394.733,
"event_sent_to_cloud_t": "2022-04-02 23:49:54",
"event_log_msg_recieved": 1648961394.732,
"event_log_msg_recieved_t": "2022-04-02 23:49:54",
"event_log_msg_passed_post_app_result": 1648961394.733,
"event_log_msg_passed_post_app_result_t": "2022-04-02 23:49:54"
},
"event_time": 1648961394,
"event_type": "Information",
"source_name": "Microsoft-Windows-Eventlog",
"computer_name": "Joe-User.rocketcyber.com",
"event_category": "Log Clear"
}
}
If we want to search details for an attribute such as event_category, you could choose Details from the search drop-down menu and enter the following text in the search value field:
attributes.event_category:Log Clear
Filtering targetResources arrays
Some events include a targetResources property, which is an array of objects. It is not appropriate to use targetResources.value (for example, targetResource.userPrincipalName:Rodri7IT@ueoficial.com), as the ".value" attribute assumes a single property rather than an array. Instead, you should use JSONPath syntax to access properties within each object in the array.
For example, since targetResources is an array, there isn't a direct userPrincipalName attribute available. This attribute exists within each item of the array and cannot be searched directly. However, you can search for a string within the array using a format such as targetResources:Rodri7IT@ueoficial.com`.
NOTE When a customer downloads a CSV file, the verdicts are represented by the numerical values 1, 2, or 3. Specifically: 1 = Informational, 2 = Suspicious, and 3 = Malicious.