Configuring USB drive monitoring (removable media)
This article indicates how to setup USB Drive log monitoring with the RocketCyber SOC.
Use cases
- Regulatory mandate requirements (PCI, HIPAA, CMMC, etc.).
- Monitor for potential data loss leaving the network.
- Monitor attack vector to prevent malware from entering the network.
Goal
Identify:
- When a USB Device is connected to a PC.
- When a USB Device is disconnected from a PC.
Overview
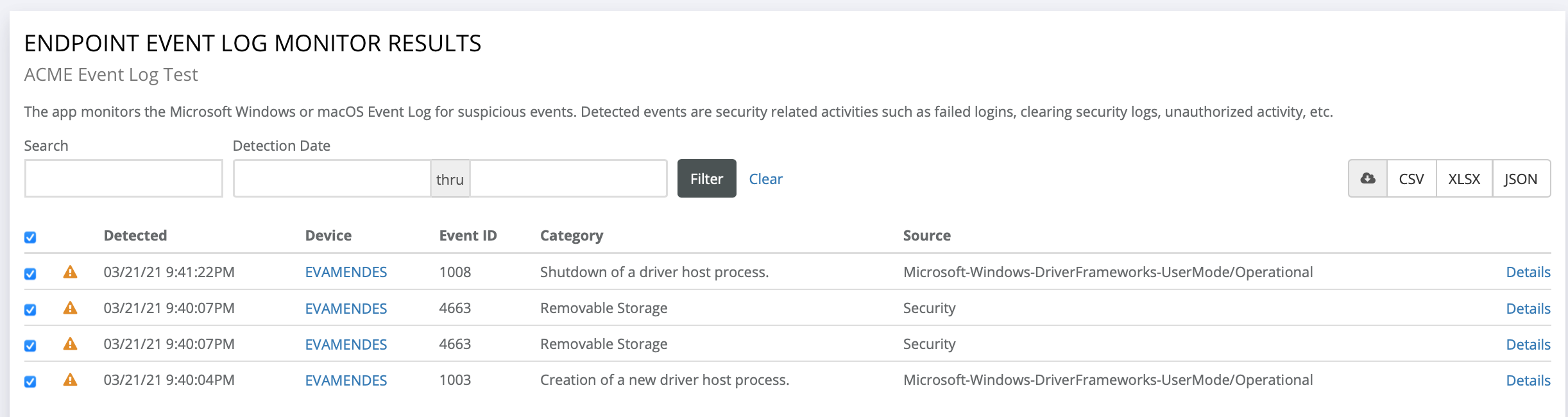
There are 3 Windows OS event log IDs that need to be added to the RocketCyber "Suspicious Event Log Monitor" app policy.
| Event ID | Description | Log Source |
|---|---|---|
| 4663 | Removable Media (General) | Security |
| 1003 | USB Media Connected | Microsoft-Windows-DriverFrameworks-UserMode/Operational |
| 1008 | USB Media Disconnected | Microsoft-Windows-DriverFrameworks-UserMode/Operational |
How to configure on Windows OS
These event logs cannot be monitored with Microsoft default settings. In order to detect such events, the auditing of these events needs to be enabled. 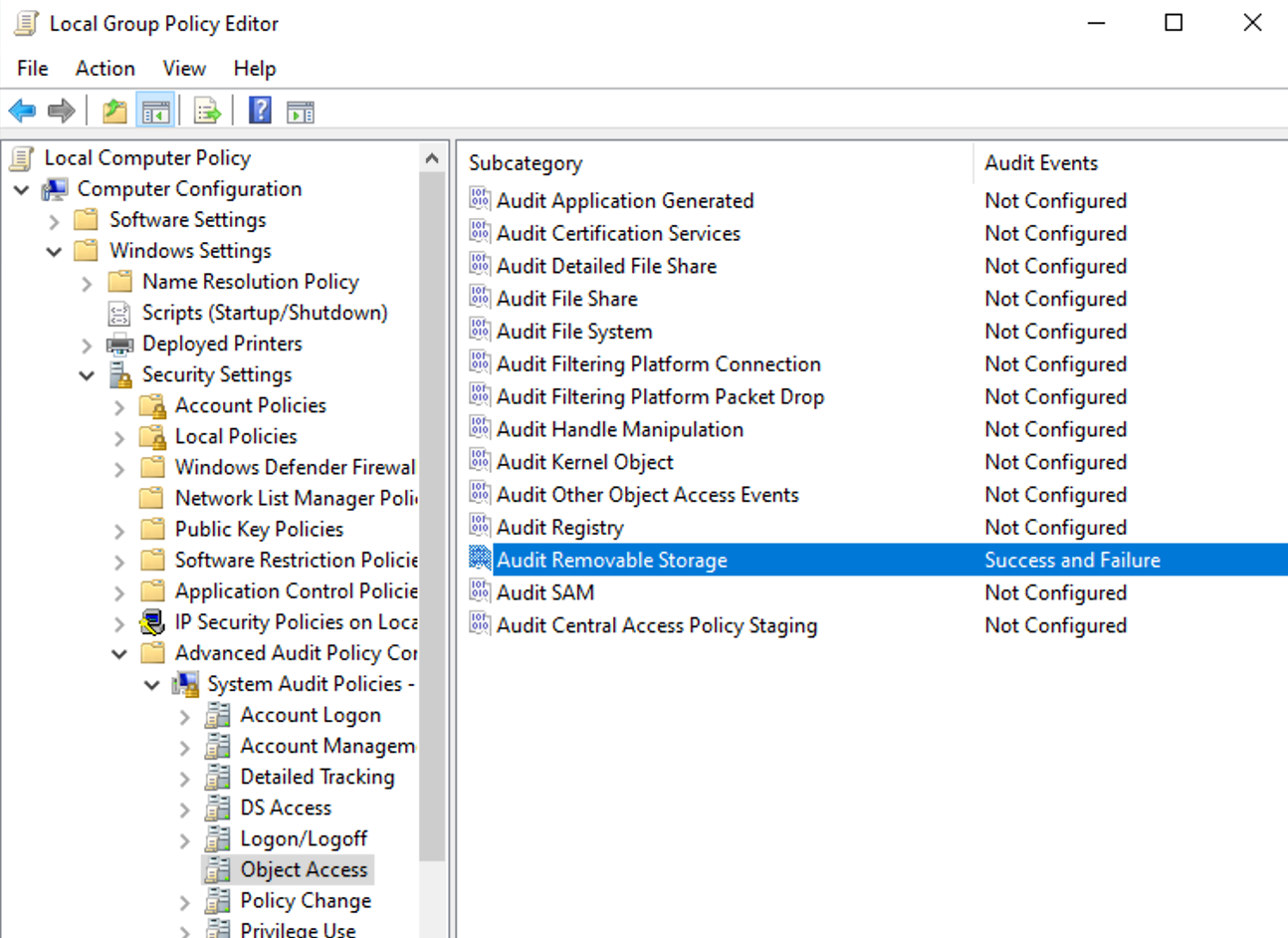
- In the Windows Start > Search field, type edit group policy.
- Open Edit group policy.
- Navigate to Computer Configuration > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Object Access > Audit Removable Storage > Success & Failure.
- Select the check box Configure the following audit events.
- Select the Success and Failure check boxes.
- Click Apply.
How to configure on the RocketCyber SOC platform
- Navigate to the correct tenant level where these detections need to take place (Provider / Organization / Device).
- Scroll down and find the Endpoint Event Log Monitor app and click the gear.
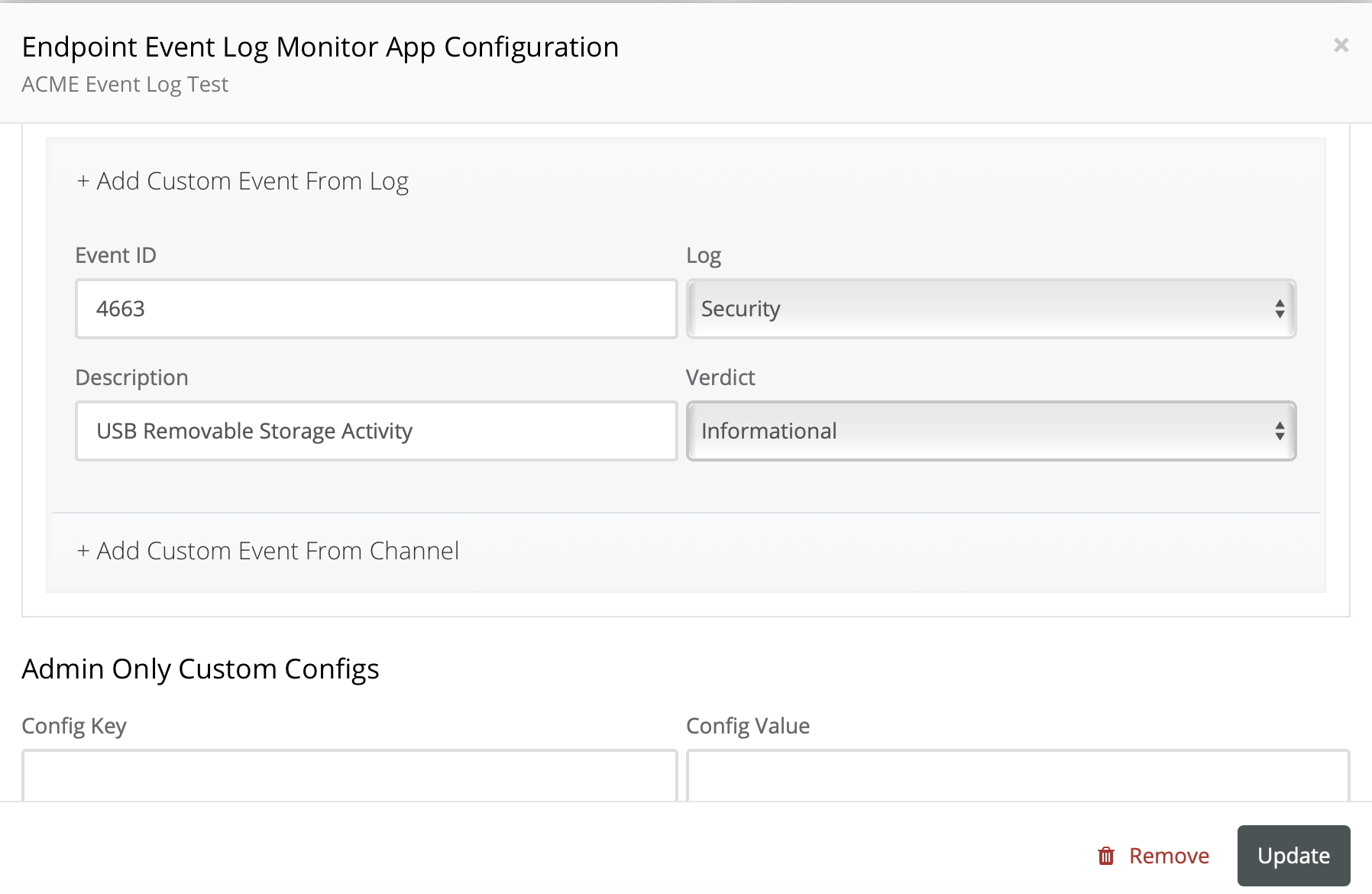
- Event ID 4663 - scroll down and click + Add Custom Event Log, configure as illustrated, then click Update.
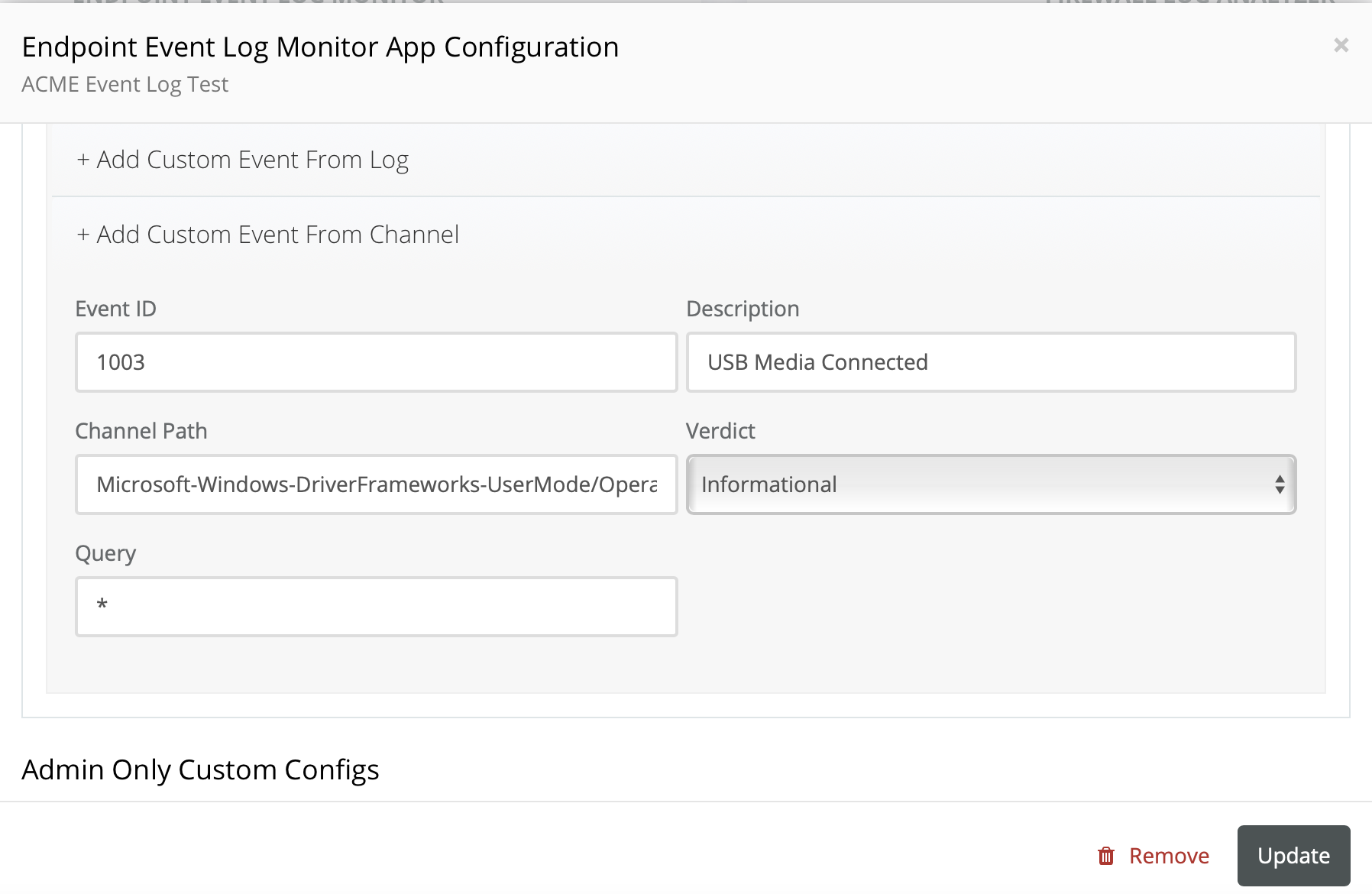
- Event ID 1003 & 1008 - These events are not obtained from the traditional Microsoft Big 3 log sources as shown above. Instead these will be configured by scrolling down to + Add Custom Event from Channel as illustrated, then click Update.
In the Channel Path field, enter Microsoft-Windows-DriverFrameworks-UserMode/Operational.
- Repeat step 4 as shown above for ID 1008.
NOTE Theoretically you have the option to choose either the Security Log Source or the Microsoft Channel Path option. Our monitoring experience is to include both options as the results (output) varies depending upon what you are trying to achieve.