Monitoring Crimson event logs on Windows
Make custom configurations with Crimson Event Logs
About Crimson Channel Logs
Windows includes two categories of event logs: Windows logs, and Applications and Services logs. This includes the event logs available in previous versions of Windows: Application, Security, and System event logs. It also includes two new logs: the Setup log and the ForwardedEvents log.
Applications and Services Logs
Applications and Services logs are a new category of event logs. These logs store events from a single application or component rather than events that might have a system-wide impact. This new category of event logs is referred to as an application's crimson channel.
The Applications and Services logs category includes four subtypes: Admin, Operational, Analytic, and Debug logs.
Events in Admin logs are of particular interest if you use event log records to troubleshoot problems. Events in the Admin log should provide you with guidance about how to respond to the events.
Events in the Operational log are also useful but may require more interpretation. Admin and Debug logs aren't as user-friendly. Analytic logs (which by default are hidden and disabled) store events that trace an issue, and often a high volume of events are logged. Debug logs are used by developers when debugging applications.
Configuring Endpoint Event Monitor for Crimson Logs
- From the RocketCyber Dashboard click the Configure button on the Endpoint Event Log Monitor App Card.
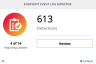
- In the App Configuration Dialog, click Add Custom Event From Channel.
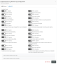
- In the Custom Event From Channel pane, enter the required information:
- Click Update or Create to save the channel event to the configuration.
Once the configuration has been saved the agents will be notified of the updated configuration and will begin monitoring for the event.