Configure Datto Ransomware Detection
Ransomware actors have become increasingly good at bypassing traditional prevention methods and gaining access to encrypt systems. Even one full encryption event can bring business to a standstill, and result in downtime, risk of reinfection, and data loss.
Datto Ransomware detection is designed to detect encryption events on endpoints where it is enabled, and mitigate the impact of the ransomware event by isolating the affected system to prevent further spread, attempting to stop the encryption process, and notifying you of the event and which files may have been encrypted before the mitigation stopped the process. This will allow you to quickly target the appropriate mitigation and recovery strategy.
How it works
Datto Ransomware detection looks for encryption events across the drives on a Windows system where it is enabled. How it reacts is based on the configuration settings in the App. An encryption and/or mitigation event will also generate an Incident, the details of the encryption event, the actions taken by the app, a summary of the affected files, and recommendations on remediation will be displayed.
Enabling the App
Datto Ransomware detection can be enabled at the provider or organization level, and can be configured at the provider level (for all organizations), the organization level, or the device level. Refer to Device-specific RocketApp configuration.The components are installed and configured once the app is enabled and configuration settings are confirmed. You can enable the app across your organizations by navigating to the App Store. Ensure the toggle appears green.
The app will now be visible in your dashboard.
Configuration settings
Once the app is enabled, you can configure the behaviors by navigating to Dashboard and clicking Configure. This will open the configuration options.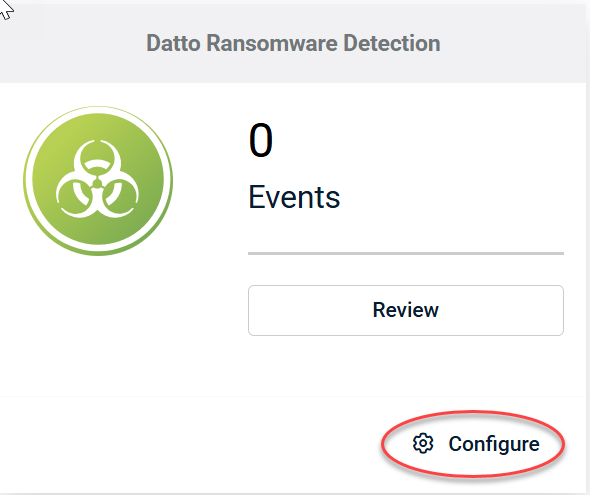
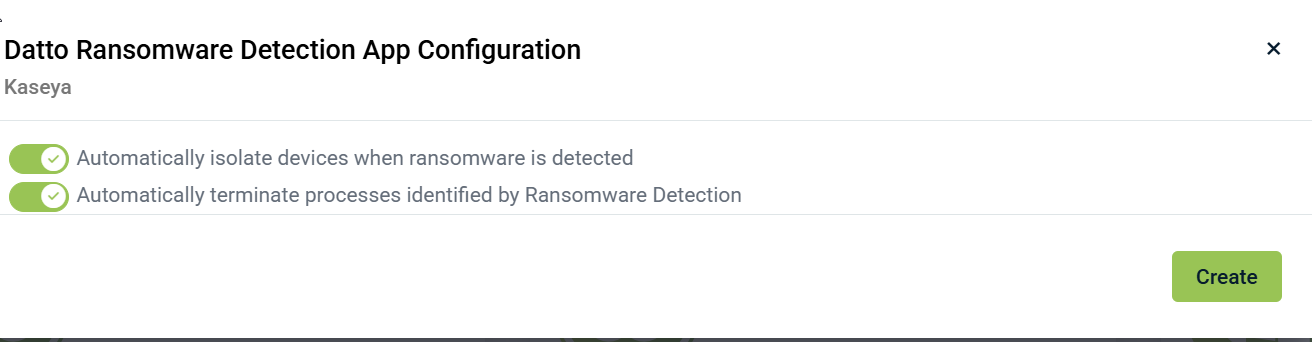
Automatically Isolate devices when ransomware is detected: This setting will use the built-in isolate function in the RocketCyber agent, you will be able to see the device was isolated in the Incident, and can reconnect the device when needed from the Devices section.
Automatically terminate processes identified by Ransomware Detection : The app will attempt to kill any processes determined to be the encrypting process. The results of the attempt will be shown in the Incident that is created(see below).
Once the configuration is confirmed, click Create. This will enable the module on all systems.
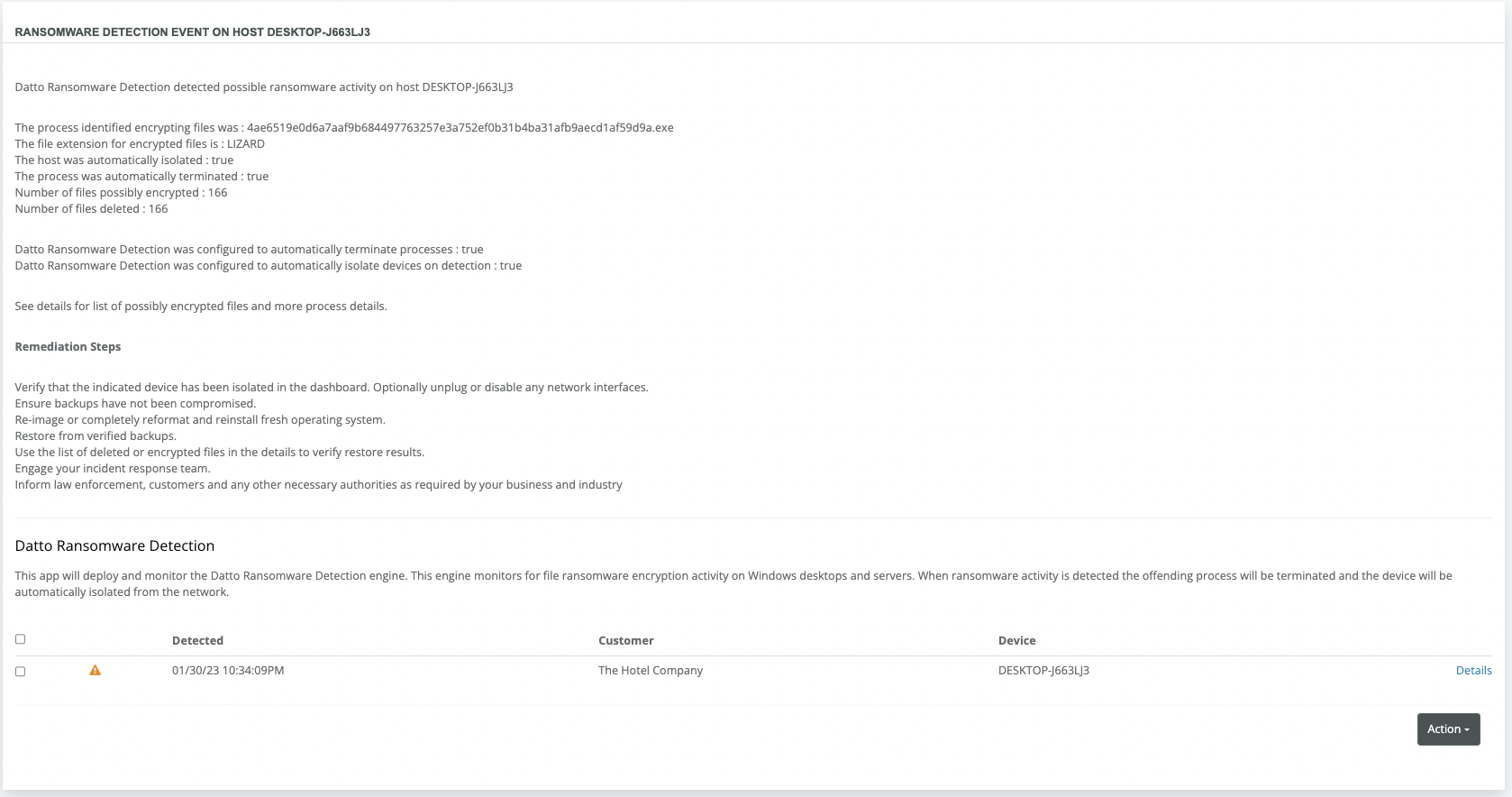
Example of incident created by Datto Ransomware Detection
The incident will contain:
- Name of the affected system
- Configured settings at the time of the corresponding event
- Remediation recommendations
You can click on the Details of the corresponding event to view information regarding:
- Files deleted by the ransomware
- Potentially encrypted files(to aid in recovery efforts)
- Details of the event and actions taken
NOTE While the app is now available, it is currently in the OFF position. This will allow you to enable for specific organizations or devices to test in your environment. If you want to enable the app across all organizations, simply navigate to the App Store and enable the app at the Provider level. If you are using Datto Ransomware from within another product, it is recommended to only have one instance enabled on an endpoint. While they can operate together, detections will generally only be picked up by one of the instances of Ransomware detection. It should be noted that the SOC will act on detections generated by RocketCyber, or from Datto EDR if you have both products.