Configuring Cisco ASA firewall (Legacy)
Disclaimer
Cisco ASA and ASDM are considered legacy technologies. ASDM reached end-of-life in 2022, and Cisco recommends migrating to Cisco Secure Firewall (Firepower Threat Defense) for next-generation security features.
Overview
RocketCyber integrates with Cisco ASA firewalls by forwarding syslog messages to the RocketCyber agent for analysis. ASA remains supported for basic firewall and VPN functionality but lacks advanced NGFW features such as application visibility, SSL decryption, and integrated threat intelligence.
ASDM (Adaptive Security Device Manager) was Cisco’s GUI for ASA configuration but is now deprecated. Cisco recommends using CLI or migrating to Firepower Management Center (FMC) for GUI-based management.
Configure Basic Syslog with ASDM
This procedure demonstrates the ASDM configuration for all available Syslog destinations.
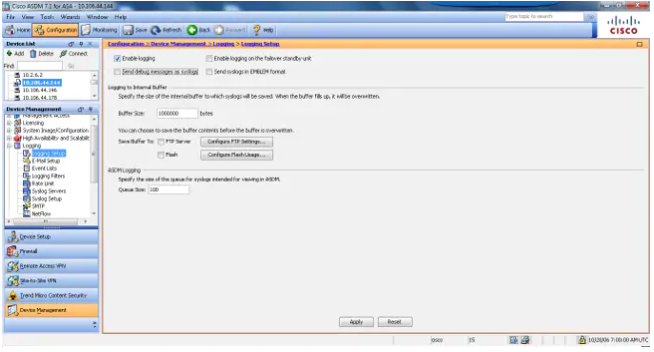
- In order to enable logging on the ASA, first, configure the basic logging parameters. Choose Configuration > Features > Properties > Logging > Logging Setup. Check the Enable logging check box in order to enable Syslog.
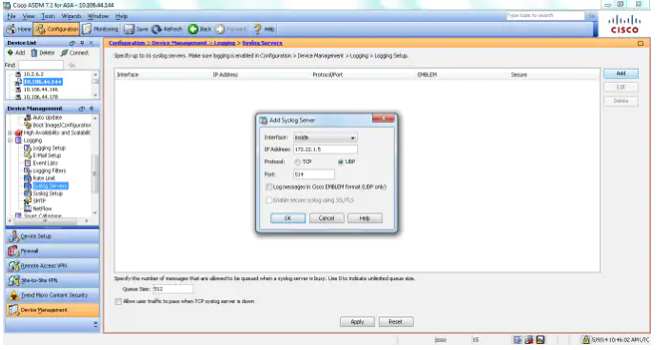
- In order to configure an external server as the destination for Syslogs, choose Syslog Servers in Logging and click Add in order to add a Syslog server.
- Choose the Appropriate Interface to send Syslog messages from.
- In the IP Address field, enter the IP address of the RocketAgent Syslog Server.
- Click on UDP
- Enter 514 in the Port field.
- Click Ok
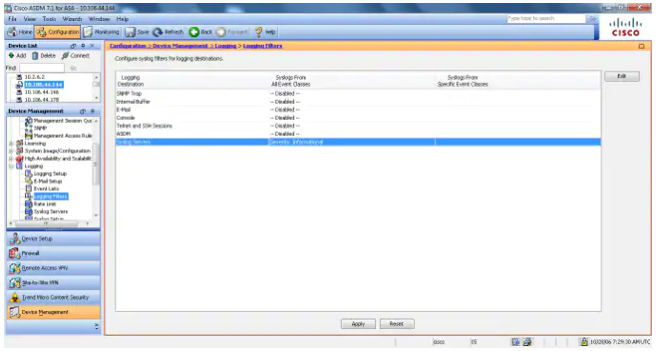
- In order to enable logs to be sent to the RocketAgent Syslog Server, choose Logging Filters in the logging section. This presents you with each possible logging destination and the current level of logs that are sent to those destinations. Choose the Logging Destination for the RocketAgent Syslog Server (Syslog Servers) and click Edit.
- Choose Informational, from the Filter on severity drop-down list. Click OK when you are done.
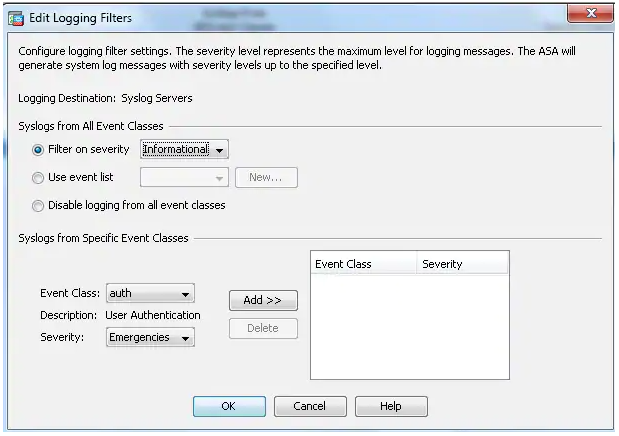
- Click Apply after you return to the Logging Filters window.
*Ensure these event IDs are enabled in the firewall in Non-Emblem logging format.
| Cisco ASA event ID | Description |
|---|---|
|
%ASA-4-400007 |
IP Fragment Attack |
|
%ASA-4-400008 |
IP Impossible Packet Attack |
|
%ASA-4-400023 |
Fragmented ICMP Traffic Attack |
|
%ASA-4-400024 |
Large ICMP Traffic Attack |
|
%ASA-4-400025 |
Ping of Death Attack Attack |
|
%ASA-4-400027 |
TCP SYN+FIN flag Attack |
|
%ASA-4-400028 |
TCP FIN only flags Attack |
|
%ASA-4-400041 |
Proxied RPC Request |
|
%ASA-4-400030 |
FTP Improper Port Specified |
|
%ASA-4-400031 |
UDP Bomb attack |
|
%ASA-4-400032 |
UDPSnorkattack |
|
%ASA-4-400033 |
UDPChargenDoS attack |
|
%ASA-6-302013 |
Reputation lookup on connecting IPs |
|
%ASA-4-400026 |
TCP NULL flags Attack |
|
%ASA-6-605005 |
Successful User login |
|
%ASA-6-605004 |
Failed User login |