Configuring Cisco Meraki
This article will describe the steps required to configure Cisco Meraki to send Syslog messages to the RocketAgent Syslog Server
To configure Cisco Meraki to send log data to RocketCyber Firewall Analyzer,
- Open your Meraki dashboard.
- Select a device.
- Navigate to Network-wide > Configure > General
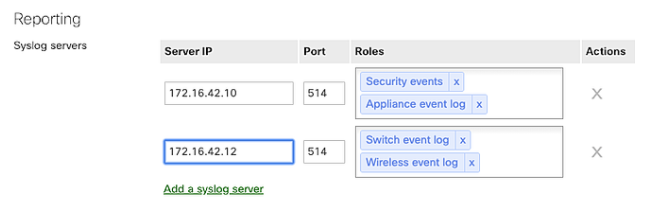
- Click Add a Syslog server.
- Type the IP address of your RocketAgent Syslog Server in the Server IP field
- Type port number 514 in the Port field.
- Choose which types of events to send in the Roles box, we require the following roles:
- Event Log —The messages from the dashboard under Monitor > Event Log.
- Flows — Inbound and outbound traffic flow-generated Syslog messages that include the source, destination, and port numbers.
- URL— HTTP GET requests generating Syslog entries.
- IDS Alerts - Sends messages related to IDS detections
The following roles are recommended:
-
- Security Event - Sends messages related to general security events
- Security Filtering File Scanned - Sends messages related to file scans
- Security Filtering Disposition Change - Sends messages related to file scan results
When the Flows role is enabled on an MX security appliance, logging for individual firewall rules can be enabled/disabled on the Security appliance > Configure > Firewall page, under the Logging column:



