August 20, 2024 RocketCyber release notes
Introducing Microsoft 365 Remediation Actions
We are very excited to announce the release of Microsoft 365 remediation actions, now available in all Microsoft 365 Login and Risk detection incidents.
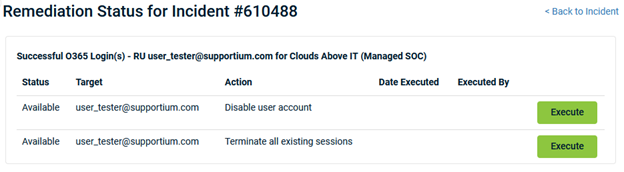
This feature was developed specifically to address the prolific threat of business email compromise (BEC). Now, in the event of suspicious or malicious activity in your Microsoft account, you can disable the user (Disable user account) and terminate all active sessions (Terminate all existing sessions) easily within the RocketCyber platform.
With a few simple clicks to execute either of these remediation actions, you quickly react to bad actors utilizing a compromised email and stop them from causing further damage to your business.
Updating your Microsoft 365 Credentials
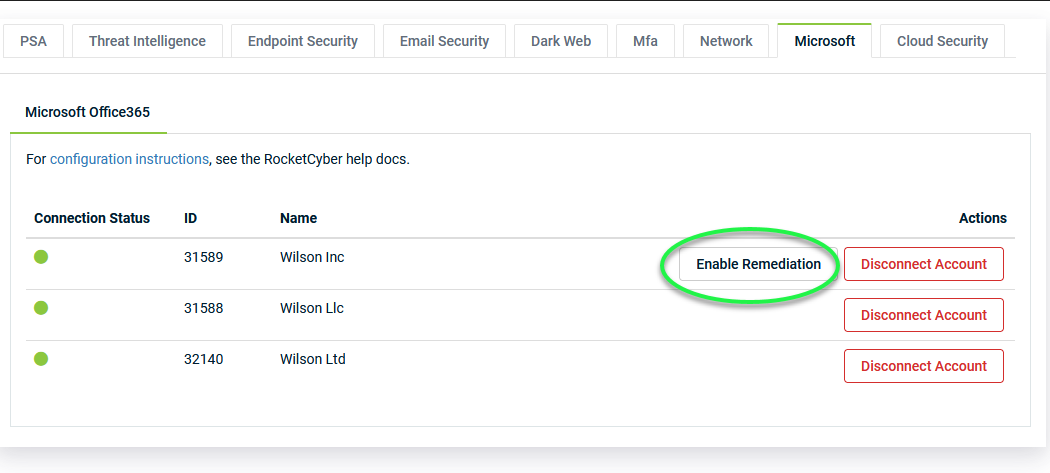
To take advantage of the new remediation features for Microsoft 365 incidents, additional permissions are required for your Microsoft 365 integrations. We have added a new Enable Remediation button on the Integrations page to make this process as easy as possible:
-
Click Integrations on the left menu and navigate to the Microsoft tab.
-
Click the Enable Remediation button next to each account for which you would like to enable this feature.
-
You will be prompted to allow a new set of permissions. Review the list and click Allow to continue.
IMPORTANT Updating permissions is entirely optional. No action is required if you do not wish to use the new remediation features. If you choose not to update permissions, your existing Microsoft 365 integrated accounts will continue to be monitored as usual.
Executing Remediation Actions
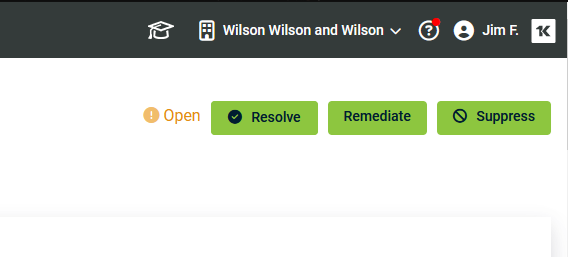
This feature uses the same workflow as our existing device remediation feature. In the details of any incident from 365 Login Analyzer or 365 Risk Detection, click Remediate.
Click Execute next to each action so they can take effect on the targeted accounts.