Verifying firewall analyzer connectivity
To verify that the firewall syslog traffic is reaching the syslog server, follow these steps:
1. Navigate to Organization Settings.
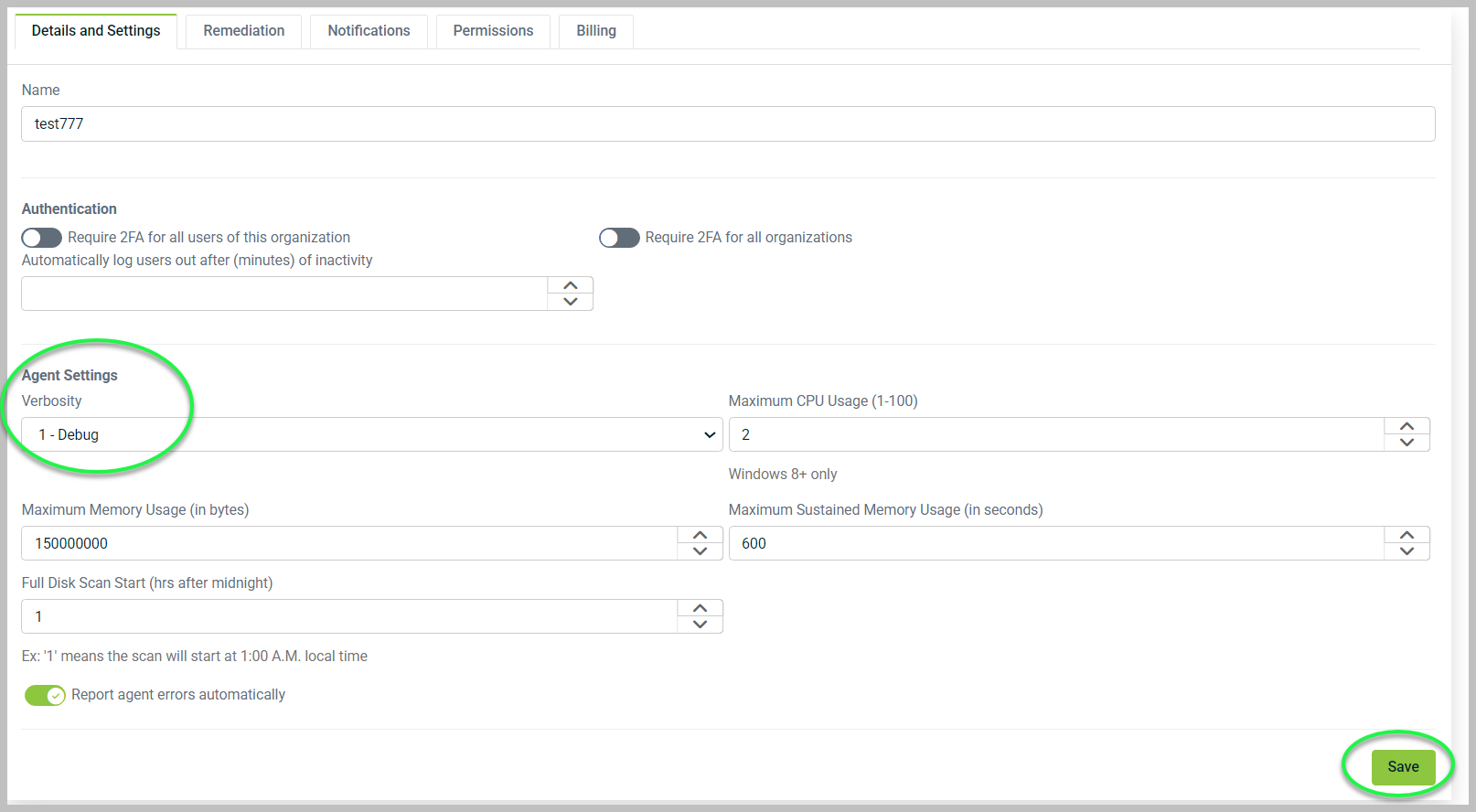
2. Go to the Details and Settings tab, then find the Verbosity drop-down menu under the Agent Settings section. Change the drop-down menu to Debug. Scroll to the bottom of the page and click Save.
3. Restart the Rocketagent in services
4. Access the syslog server machine and navigate to c:\programfiles\rocketagent\logs\syslogsvr file
5. Search for raw syslog in the text file you find. Look for successful binding messages followed by entries that identify the firewall. This indicates that it will register in the RocketCyber portal.
For example, you might see entries like this:
[2023-01-06][11:30:21][00:00:29] [info] syslogsvr: Binding successful, waiting for log messages on 192.168.1.10:540
[2023-01-06][11:30:21][00:00:29] [debug] syslogsvr: mac_address in send_arp_request is XX:XX:XX:XX:XX:XX
[2023-01-06][11:30:21][00:00:29] [debug] syslogsvr: raw_syslog: <30>device="ABC" date=2023-01-06 time=11:30:25 timezone="EST" .........
[2023-01-06][11:30:21][00:00:29] [debug] syslogsvr: determined is a sophos firewall
[2023-01-06][11:30:21][00:00:29] [debug] syslogsvr: sophos format is sophos_xg
[2023-01-06][11:30:21][00:00:29] [debug] syslogsvr: should_register_firewall - first device allow registration
f the log only shows "waiting for log messages" and no raw syslog traffic follows, check the firewall configuration to ensure it is set up to send traffic to the syslog machine. An example log entry to look for is:
[info] syslogsvr: Binding successful, waiting for log messages on 192.168.xxxx.xxx:514
Each firewall brand will have a specific set of security events that populate the app. Other events not listed will be filtered out.
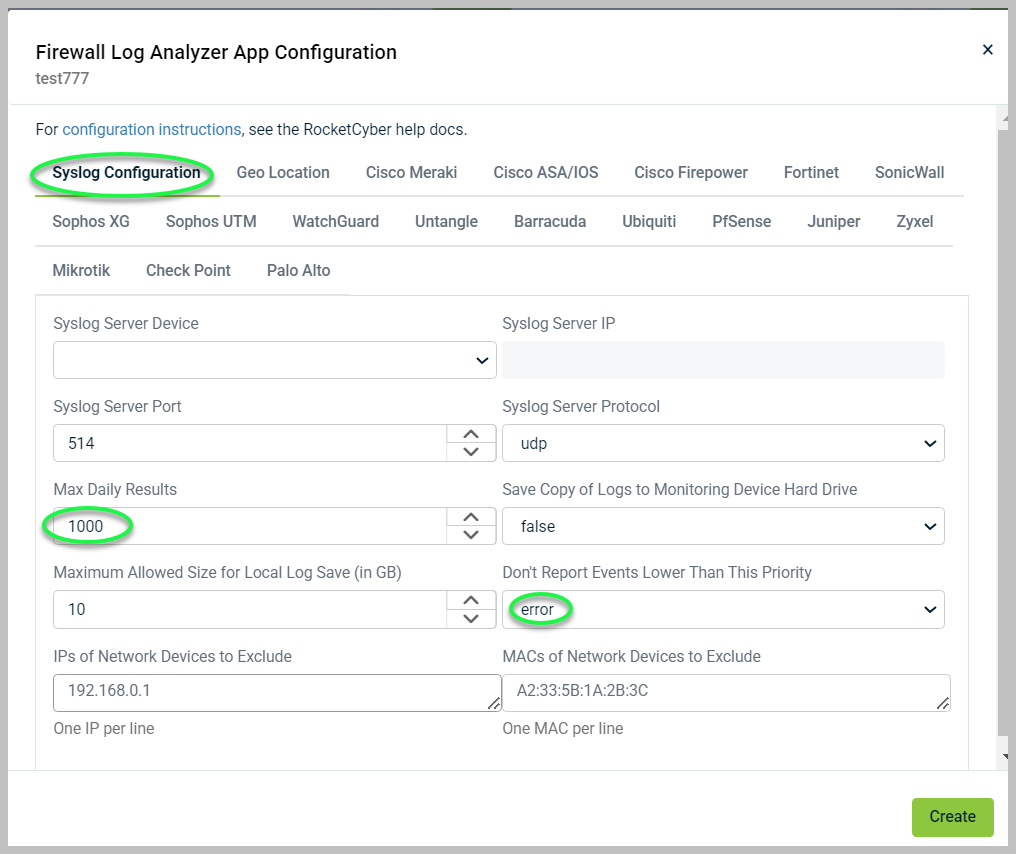
If you see events listed, check the configuration settings under the Syslog Configuration tab. You can lower the reporting priority and increase the maximum daily results.
Common Problems
-
A host-based firewall might be blocking incoming traffic on the machine. By default, the Firewall Analyzer configures the Windows Firewall to allow inbound syslog traffic on the configured ports and protocols. To verify that the rule was created properly, open the Windows Firewall, click Advanced, and look for a rule named RocketCyber Syslog Allow. If you are using another endpoint security product that has a host-based firewall, you will need to manually configure it to allow inbound traffic on the configured port and protocol.
- Ensure that you are not mistakenly entering the firewall's IP address instead of the monitoring device's IP.
- Confirm that you have added a syslog forwarding rule on the firewall to send the logs to the Firewall Analyzer.
- By default, our filtering removes informational messages that do not require any action from you. If you want to verify that everything is functioning correctly, go to the configuration menu and change the Don't Report Events Lower Than This Priority setting to Info.
- If you are using a firewall that allows you to configure the severity level of Syslog events being sent, set severity to info
- If needed, try restarting the agent
One exception to filtering at the severity level is the IP Reputation Lookup. Traffic from malicious IPs will be displayed even if it has an Info priority level. This setting can be turned off under the tab for your firewall brand of firewall by toggling the IP reputation lookup to OFF.