Using the dashboard
The dashboard offers a quick overview of all your devices, configured apps, events, and open incidents. It enables prompt identification of potential threats and highlights areas for necessary improvement.
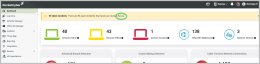
Open Incidents banner
You will see a yellow Open Incidents banner in your dashboard when new incidents are pending review. These incidents indicate suspicious or malicious activities identified and escalated by the Security Operations Center (SOC) from looking at your all events and data. It is essential to review, remediate, and resolve these incidents promptly to maintain security integrity. Click Review to proceed.
When clicking Review, you will be directed to the Incidents page. For more information on how to suppress and resolve incidents, refer to Managing incident suppression.
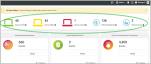
Monitored devices and accounts
Below the yellow Open Incidents banner, you will find a summary of your assets: Devices Online, Devices Offline, Devices Isolated, Office 365 Mailboxes, and Network Devices.
Clicking the small i icon next to each device will direct you to the Agents page, which is located within the Devices.
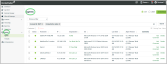
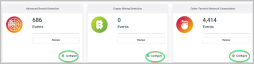
Dashboard tiles
The tiles displayed on your dashboard represent a combination of RocketCyber's native applications, Office 365 tenants, and any integrations or optional applications you've added from RocketCyber's App Store. They are mainly informational. The data that appears on the tile is the information generated by the apps as events occur. Depending on the number of devices you've deployed, you may receive numerous events. Click Review for more detailed data about these events.
NOTE: If you have configured an integration but have not enabled its app, the SOC team will not be able to monitor it, and it will not populate on your dashboard.
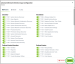
Click Configure to customize the settings for each app. We strongly recommend using the default configurations, but if changes are necessary, our Product Support team is available to provide best practices.
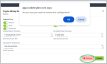
Once you click Configure,, a pop-up window will appear for you to make your changes. After completing your adjustments, ensure you click Update in the bottom-right corner.
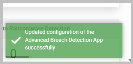
You will receive a success message at the bottom right corner of the main app page confirming that your changes have been successfully updated.
To remove a configuration, click Remove in the bottom-right corner. You will then see a prompt to either continue or cancel the removal.
Some of the apps available in your dashboard include the following:
Advanced Breach Detection
Using the Advanced Breach Detection app, the RocketCyber agent utilizes proprietary technology to monitor Windows, Mac, and Linux devices for indications of a compromised device. Leveraging the MITRE ATT&CK® framework, the agent collects activity data on each device and forwards the data to the SOC, where it is triaged and analyzed. We recommended that you enable its T1098 option.
Cyber Terrorist Network Connections
This app detects network connections to various nation-states known to engage in cyber terrorist activities. It compares IP address communications against real-time threat feeds to discover connections to malicious IPs, C2 servers, botnets and other backdoor services.
Endpoint Event Log Monitor
With this app, the agent monitors the Microsoft Windows, macOS and Linux Event Logs for suspicious events. Examples of suspicious events include failed logins, cleared security logs, and unauthorized activities. The logs are forwarded to the SOC for analysis, and logs are stored for historical auditing purposes. Additionally, you can add custom events from here.
For more detailed information about the apps in your dashboard, refer to Default apps.
In summary, events play a crucial role on our dashboard. The dedicated SOC team utilizes these events to effectively triage and escalate any open incidents as necessary. Rather than striving for zero events, we should recognize them as valuable tools for monitoring our environment. Our main priority should be on managing open incidents and ensuring that we stay on top of them.