Managed SOC incident response guide
Introduction
RocketCyber SOC team works on the IT PARTNER’s behalf to detect, respond, and remediate critical cybersecurity incidents via all tools and methods available. The arsenal of the RocketCyber’s incident response team is constantly adapting to global threat patterns by developing new apps and integrations that blend machine and human learning and actions. The combined automated and manual approach provides a redundant layer of action to effectively detect, investigate, contain, report, and recover.
We base our incident response model on the National Institute of Standards and Technology (NIST) Framework of Improving Critical Infrastructure Cybersecurity and the MITRE ATT&CK® Framework, among others. The frameworks enable organizations to apply the principles and best practices of risk management to improving the security and resilience of critical infrastructure. It provides organization and structure to today’s multiple approaches to cybersecurity by assembling standards, guidelines, and practices that are working effectively in industry today.
Partnership
RocketCyber’s success depends heavily on close collaboration with the IT Partner and their ability to implement the strictest security measures possible. RocketCyber will constantly advise its partners to fortify their network defenses against cyber threats via the following methods:
-
Deploy and maintain next generation endpoint protection
-
Implement strict firewall policies at the network edge
-
Train employees to be vigilant
-
Activate MFA for all admin and user accounts
-
Frequently backup and use continuous data protection software
-
Practice a least-privilege approach
-
Implement a plan for continuous operations
-
Always install system updates
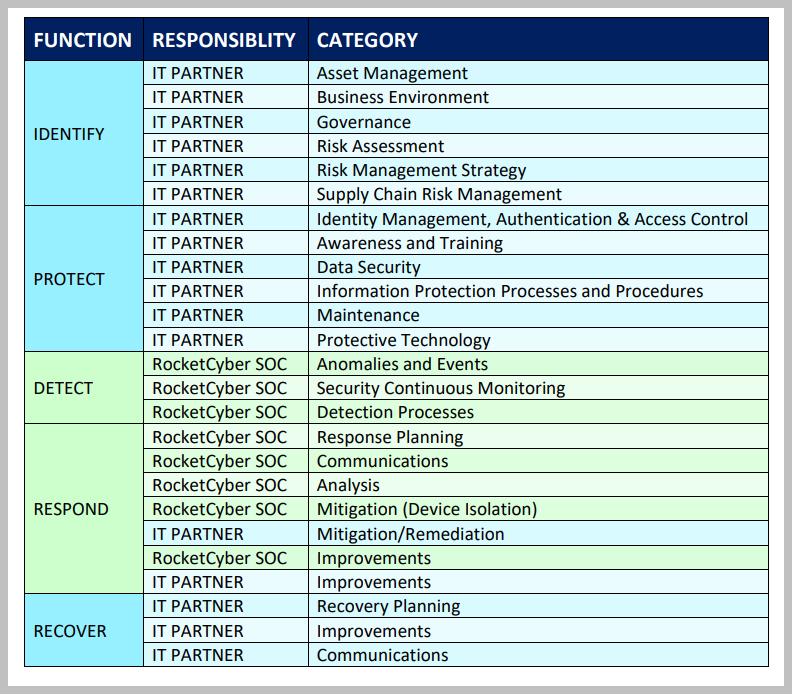
Areas of Responsibility
Based on the NIST model we summarize the areas below that depict responsibilities of RocketCyber and the IT PARTNER to ensure the most effective ability to DETECT, RESPOND, and RECOVER to a cyber event.
Detections
A threat event has the potential for causing consequences or impact. Events include unauthorized access to computers, unauthorized use of system privileges and execution of malware that destroys, encrypts a system, or steals data. Think of an event as an observable occurrence, such as when a failed login to a computer occurs. While this could be either unintentional or intentional, both are considered events.
A security incident is a violation or imminent threat of security policies or industry best practices. Incident examples include the following:
-
Denial of service: an attacker sends high volumes of connection requests to a server, resulting in a crash.
-
Phishing: employees are enticed to click and open EMAIL/PSA attachments or links resulting in malware deployment or establishing a connection with external systems.
-
Malware: Type of application designed to perform a variety of malicious tasks: create persistent access, spy on the user, create disruption, etc. The most notable form of Malware is Ransomware.
-
Ransomware: an attacker obtains unauthorized access, encrypting the system and asking for a financial sum of money before the computer is decrypted and operational.
-
RDP hijacking: involves the attacker “resuming” a previously disconnected RDP session. This allows the attacker to get into a privileged system without having to steal the user’s credentials.
-
PowerShell: Attackers commonly use command and script interpreters such as PowerShell to execute malicious commands, run scripts, and binaries when carrying out an attack.
-
PowerShell without PowerShell: PowerShell commands and scripts can be executed by loading the underlying
System.Management.Automation namespace. As a result, this eliminates the need to spawn powershell.exe.
-
Business EMAIL/PSA Compromise (BEC): an attacker has gained unauthorized access to an employee’s
EMAIL/PSA.
-
Man-in-the-middle attack (MITM): attacker intercepts the communication between two parties to spy on the victims, steal personal information or credentials, or alter the conversation in some way.
-
Zero-day exploit: Cyber-criminals learn of a vulnerability that has been discovered in certain widely-used software applications and operating systems, and then target organizations who are using that software to exploit the vulnerability before a fix becomes available.
-
Cryptojacking: Cyber criminals compromise a user’s computer or device and use it to mine cryptocurrencies, such as Bitcoin.
-
DNS Tunnelling: Is a sophisticated attack vector that is designed to provide attackers with persistent access to a given target. Since many organizations fail to monitor DNS traffic for malicious activity, attackers can insert malware into DNS queries (DNS requests sent from the client to the server). The malware is used to create a persistent communication channel that most firewalls are unable to detect.
-
Drive-by Attack: A "drive-by-download" attack is where an unsuspecting victim visits a website which in turn infects their device with malware. The website in question could be one that is directly controlled by the attacker, or one that has been compromised. In some cases, malware is served in content such as banners and advertisements. These days exploit kits are available which allow novice hackers to easily set up malicious websites or distribute malicious content through other means.
-
Eavesdropping attack: Sometimes referred to as “snooping” or “sniffing”, an eavesdropping attack is where the attacker looks for unsecured network communications to intercept and access data that is being sent across the network. This is one of the reasons why employees are asked to use a VPN when accessing the company network from an unsecured public Wi-Fi hotspot.
Cyber Threat Intelligence
One of the approaches we follow is MITRE ATT&CK Mapping to help us understand adversary behavior as a first step in protecting networks and data. The MITRE ATT&CK® framework is based on real-world observations and provides details on 100+ threat actor groups, including the techniques and software they use. It helps identify defensive gaps, assess security tool capabilities, organize detections, hunt for threats, or validate mitigation controls.
ATT&CK describes behaviors across the adversary lifecycle, commonly known as tactics, techniques, and procedures
(TTPs). These behaviors correspond to four increasingly granular levels:
-
Tactics represent the “what” and “why” of an ATT&CK technique or sub-technique. They are the adversary’s technical goals, the reason for performing an action, and what they are trying to achieve. For example, an adversary may want to achieve credential access to gain access to a target network. Each tactic contains an array of techniques that network defenders have observed being used in the wild by threat actors.
-
Techniques represent how an adversary achieves a tactical goal by performing an action. For example, an adversary may dump credentials to achieve credential access. Techniques may also represent what an adversary gains by performing an action. A technique is a specific behavior to achieve a goal and is often a single step in a string of activities intended to complete the adversary’s overall mission.
-
Sub-techniques provide more granular descriptions of techniques. For example, there are behaviors under the OS Credential Dumping technique that describe specific methods to perform the technique. Sub-techniques are often, but not always, operating system or platform specific. Not all techniques have sub-techniques.
-
Procedures: how a technique or sub-technique has been used. They can be useful for replication of an incident with adversary emulation and for specifics on how to detect that instance in use.
The steps we follow are the following:
-
Find the behavior. Searching for signs of adversary behavior is a paradigm shift from looking for Indicators of Compromise (IOCs), hashes of malware files, URLs, domain names, and other artifacts of previous compromise. The RocketCyber Agent is collecting signs of how the adversary interacted with specific platforms and applications to find a chain of anomalous or suspicious behavior prior to damage to the customers’ businesses.
-
Research the Behavior. Additional research may be needed to gain the required context to understand suspicious adversary or software behaviors. Use additional resources integrated with RocketCyber’s platform and/or external resources when needed, to gain information on the potential threat.
-
Identify the Tactics. Comb through the report to identify the adversary tactics and the flow of the attack. To identify the tactics, we focus on what the adversary was trying to accomplish and why. Was the goal to steal the data? Was it to destroy the data? Was it to escalate privileges?
-
Identify the Techniques. After identifying the tactics, review the technical details associated with how the adversary tried to achieve their goals. For example, how did the adversary gain the Initial Access foothold? Was it through spear-phishing or through an external remote service? Drill down on the range of possible techniques by reviewing the observed behaviors in the report.
-
Identify the Sub-techniques. Review sub-technique descriptions to see if they match the information in the report. Does one of them align? If so, this is probably the right sub-technique. Depending upon the level of detail in the reporting, it may not be possible to identify the sub-technique in all cases. Read the sub-technique descriptions carefully to understand the differences between them. For example, Brute Force includes four subtechniques: Password Guessing, Password Cracking, Password Spraying, and Credential Stuffing.
-
Take or recommend remediation steps depending on the identified threat(s).
Event Data Collection, Analysis and Triage (DETECT)
Triage is the investigation of a threat event, resulting in a verdict of malicious, suspicious, or benign. Events defined as malicious or suspicious are considered an incident. Events are generated throughout the day and span networks, endpoints (computers) and cloud applications.
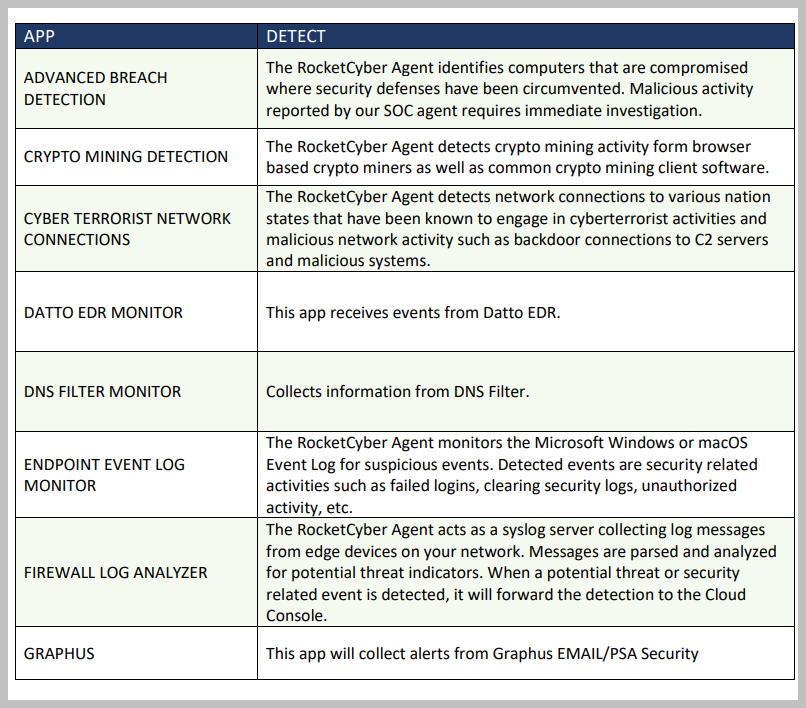
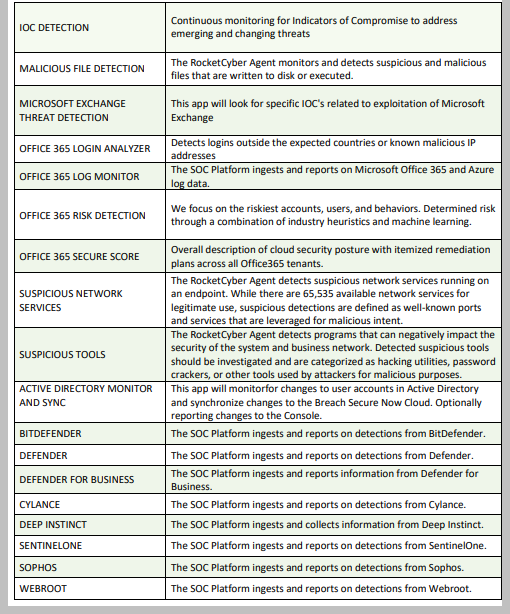
The RocketCyber SOC utilizes multiple cyber intelligence feeds that help enhance many of the services below to detect new emerging threats. The RocketCyber agent provides continuous monitoring for suspicious or malicious behavior and presents these findings in data that can be actioned through automation or human analysts.
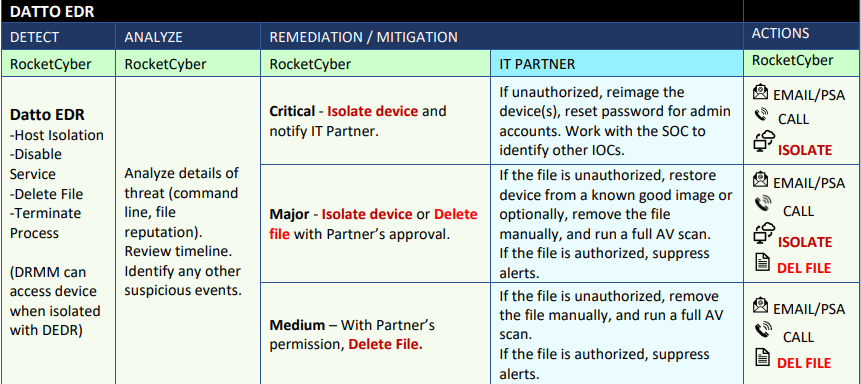
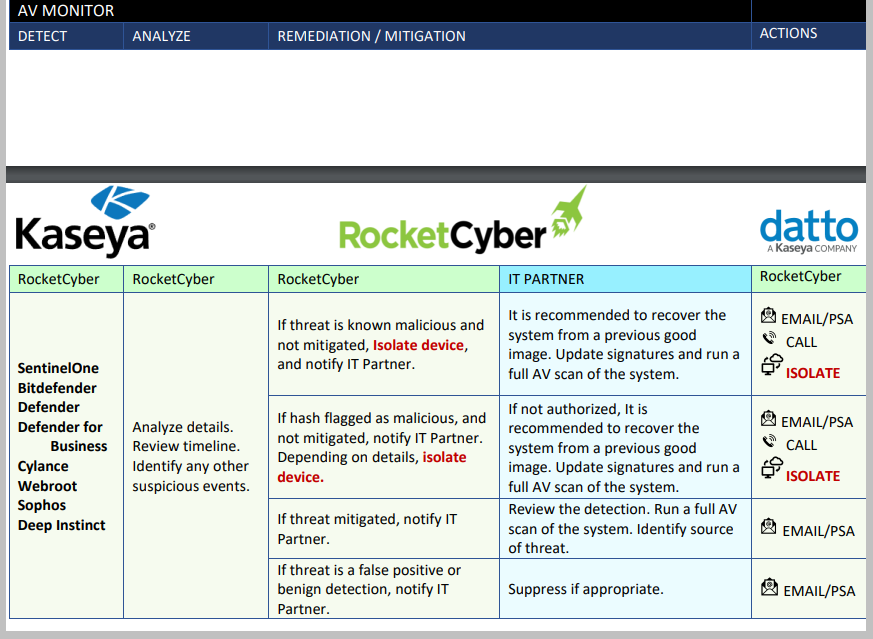
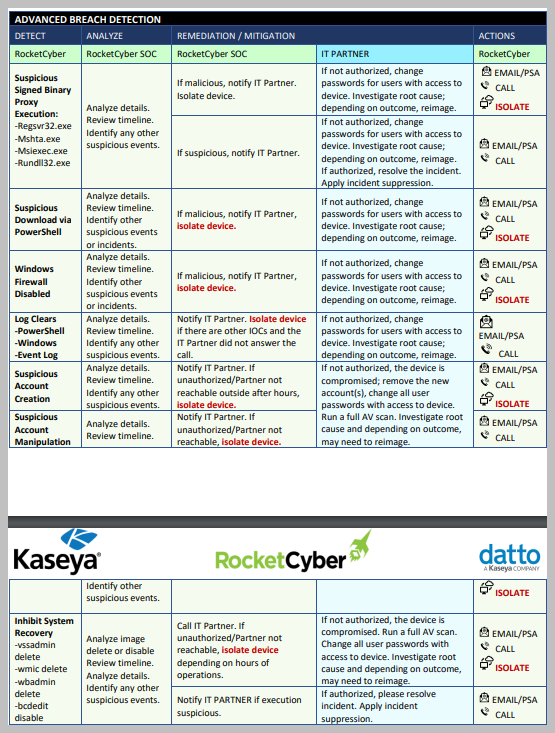
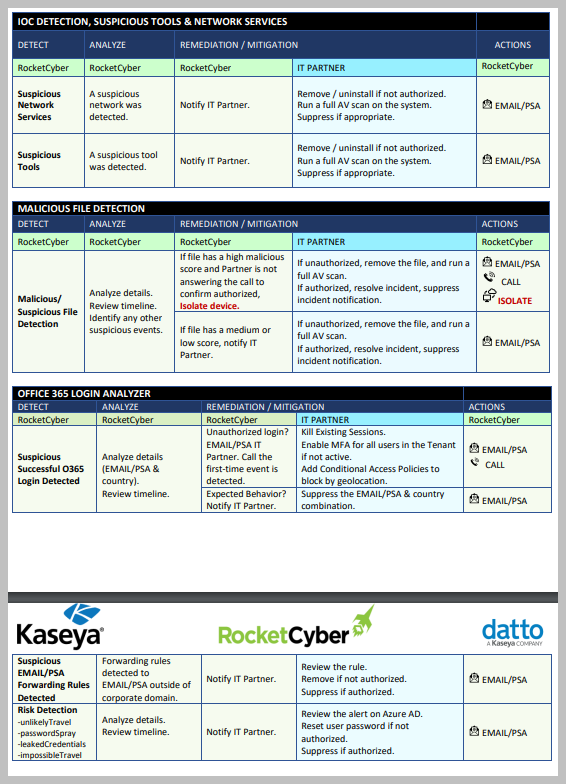
Below is a list of ever-evolving services that the RocketCyber Platform and SOC team are constantly monitoring, triaging, and responding to. Should a serious threat be found, the RocketCyber agent can isolate the device from the rest of the network. This allows further investigations without exposing threats to the rest of the customer systems.
Incident Response (RESPOND)
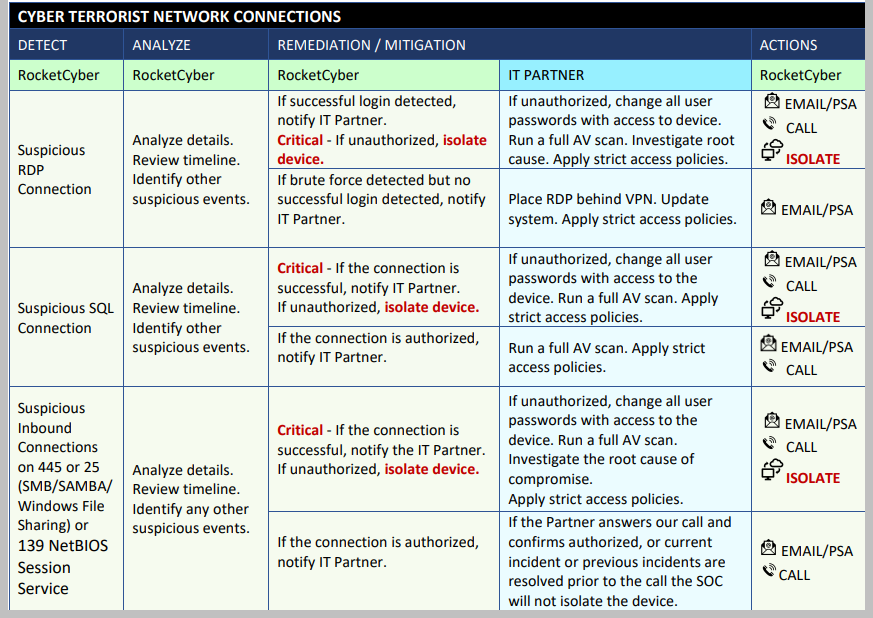
The threat landscape and attacker’s techniques are constantly evolving. While it is not feasible to list every attack and response scenario, the tables below outline common attack techniques and the anticipated actions of the RocketCyber SOC team and the IT Partner. While the list is not exhaustive, please use this as a guideline of what to expect when incidents are detected via the RocketCyber SOC platform.
When calling, the SOC will call all available numbers in the Notifications section. If a critical threat to a business system is detected, the SOC will disconnect the device from network to stop the spread of the threat even in the eventwhen no one can be reached, unless otherwise specified by the IT Partner in the Notifications Tab > Special Instructions field.
Upon generation of an Incident (PSA ticket or Email Notification), the RocketCyber SOC team will determine if the event qualifies as an Indicator of Compromise (IOC).
Please note the following:
-
If the event(s) indicate critical IOC(s), the SOC will further escalate the incident by calling the Partner and isolating device(s). For every situation that requires isolation, the SOC will create a ticket to enable 2-way communication between the Partner contacts in the Permissions Tab and the SOC.
-
After the initial IOCs were detected, the analysts will conduct an in-depth investigation to look for any other unusual events (we do not recommend archiving of events as they auto-archive on their own every 35 days).
-
Based on what it finds, the SOC will isolate the device(s) if:
-
The provider does not answer the call to confirm action(s) are authorized.
-
The SOC cannot determine with 100% certainty that any stages of an attack are not in progress based on the incidents and events found in the customer’s dashboard at the time.
-
-
The Apps serve as event collectors; the SOC triages the data in the apps to identify any unusual activity that might require further investigation. If events of interest are discovered and action by the Partner will be required, a logic rule will be created to generate notifications automatically.
-
The SOC factors the time-zone for the business and after-hours executions in the decision-making process.
-
We strongly recommend that the RocketCyber agent be installed on all devices: servers, local computers, and remote computers used for remote access.
Remediation (RESPOND)
Device Isolation
-
RocketCyber Managed SOC can isolate devices on a customer’s network that have a RocketCyber and/or Datto EDR Agent installed. The SOC uses host isolation to prevent the spread of malicious code by preventing a compromised machine from communicating to other network devices on the Internet or the Customer’s network.
-
The isolated machine will maintain connectivity to the corresponding platform and allow the SOC or the Partner to reconnect the device. Unless the Partner opts-out in Special Instructions, the SOC will isolate potentially compromised devices.
File Deletion
-
RocketCyber platform supports deleting some applications or files.
-
Datto EDR platform supports deleting files detected with the Datto EDR Reputation module.
Alerts > Alert Detail > Respond > Delete File
Antivirus Actions
-
RocketCyber or Datto EDR can run a Windows Defender AV quick or full scan if the integration is enabled.
Suppression
-
RocketCyber Notification/Incident Suppression:
-
Datto EDR Suppressing alerts:
Recommended Mitigations
CISA and FBI recommend that network defenders consider applying the following best practices to strengthen the security posture of their organization's systems whenever feasible:
-
Provide social engineering and phishing training to employees.
-
Consider drafting or updating a policy addressing suspicious EMAIL/PSAs that specifies users must report all suspicious EMAIL/PSAs to the security and/or IT departments.
-
Mark external EMAIL/PSAs with a banner denoting the EMAIL/PSA is from an external source to assist users in detecting spoofed EMAIL/PSAs.
-
Implement Group Policy Object and firewall rules.
-
Implement an antivirus program and a formalized patch management process.
-
Implement filters at the EMAIL/PSA gateway and block suspicious IP addresses at the firewall.
-
Adhere to the principle of least privilege.
-
Implement a Domain-Based Message Authentication, Reporting & Conformance validation system.
-
Segment and segregate networks and functions.
-
Limit unnecessary lateral communications between network hosts, segments, and devices.
-
Consider using application allowlisting technology on all assets to ensure that only authorized software executes, and all unauthorized software is blocked from executing on assets. Ensure that such technology only allows authorized, digitally signed scripts to run on a system.
-
Enforce multi-factor authentication.
-
Enable a firewall on agency workstations configured to deny unsolicited connection requests.
-
Disable unnecessary services on agency workstations and servers.
-
Implement an Intrusion Detection System, if not already used, to detect C2 activity and other potentially malicious network activity
-
Monitor web traffic. Restrict user access to suspicious or risky sites.
-
Maintain situational awareness of the latest threats and implement appropriate access control lists.
-
Disable the use of SMBv1 across the network and require at least SMBv2 to harden systems against networ propagation modules used by TrickBot.
Conclusion
We hope you enjoyed our Incident Response Guide. Reemphasizing our strategy to provide you with the best service with the most effective and efficient package to address your cybersecurity needs.
We look forward to performing our part in protecting your networks and data. We thank you for your Partnership and for engaging us to provide a service to one of the most critical aspects of your business operations.
Please contact RocketCyber if you have any Platform issues or require assistance with an Active Security Incident. Support is available Mon-Fri 8:00 AM – 7:00 PM EST.
The SOC is available 24x7 to monitor and respond to security incidents.
Create a ticket:
Support (Platform Issues, Integrations):
Support (Platform Issues, Integrations)
SOC (Active Security Events/Incidents):
SOC (Active Security Events/Incidents):
Or call us:
RocketCyber Support
US Toll-Free: (877) 282-8857 1, 7, 1, 2 - Mon-Fri 8:00 AM to 7:00 PM
RocketCyber Managed SOC (Active Security Incidents Assistance):
US Toll-Free: (877) 282-8857 1, 7, 1, 1
US Direct: +1 786 673 4043 (Outbound Caller ID)
EU Direct: +44 330 912 1898
AU Direct: +61 2 8000 9389