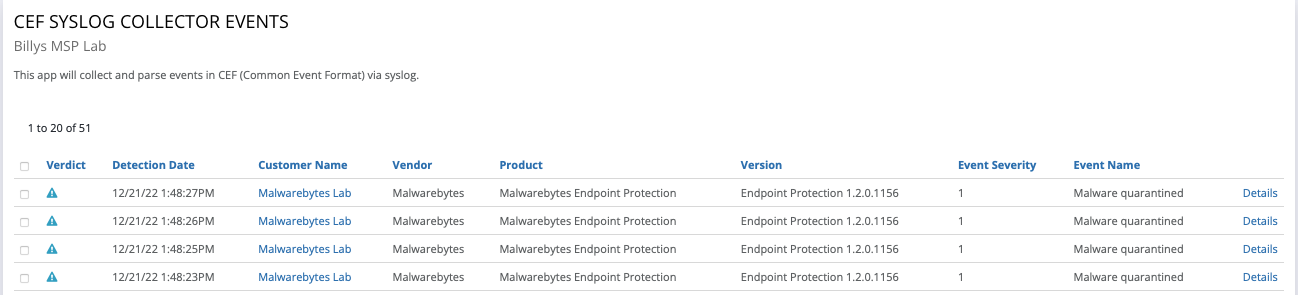
Configuring Malwarebytes EDR
This article describes the steps required to configure Malwarebytes to send Syslog messages
to the RocketCyber CEF Syslog Collector. Refer to Configuring the RocketCyber Syslog Collector.
The following steps enable Malwarebytes threat data to be sent to the RocketCyber SOC platform per tenant.
- Open Malwarebytes (Nebula) console
* If you are using Malwarebytes (OneView) multi-tenant console, navigate to sites and click on 'launch site'. This will grant you access to Nebula where configuration is needed.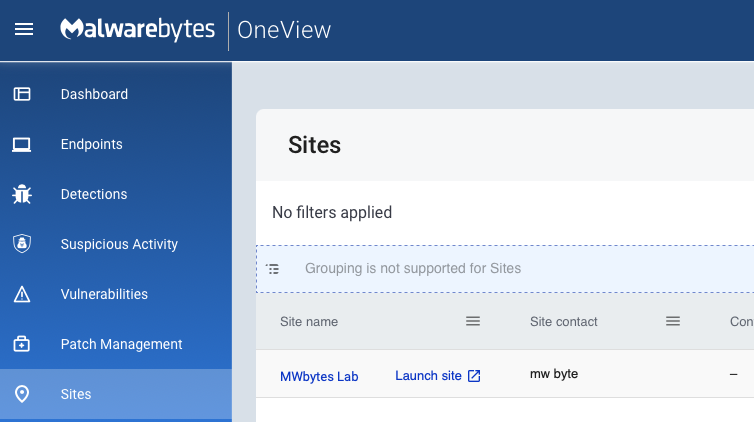
- Navigate to Settings / Syslog Logging
- Click Add, then Select a 'Windows' endpoint, then click Assign.
- Click Syslog Settings in top right corner.
- Fill in required details:
- IP Address: x.x.x.x (a Static IP is recommended)
- Port: 514 is usually the default, however if you are using the RocketCyber Firewall Analyzer for this organization on the same computing device for SYSLOG collection, we recommend a different port such as 541 or 551
- Protocol: UDP is recommended
- Severity: 1 was used for testing this integration. This setting determines the Severity of all Malwarebytes events sent to RocketCyber CEF syslog collector.
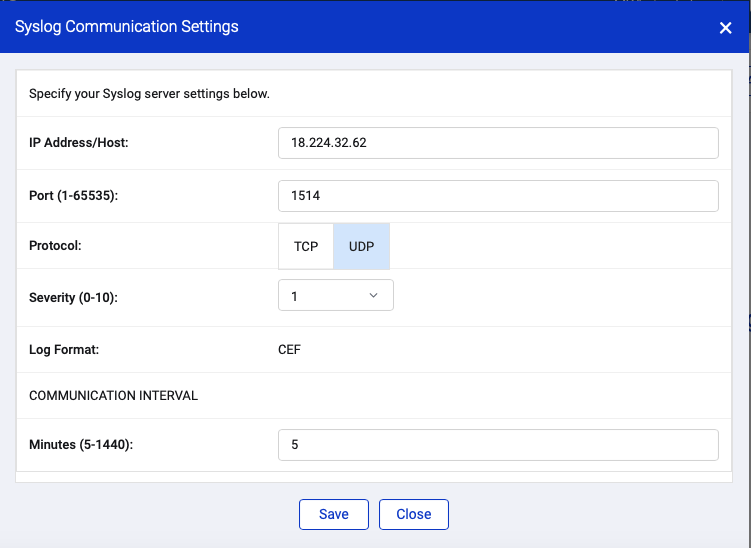
- Communication interval: 5 (minutes) is recommended. * note if this endpoint is offline and/or unable to communicate to the Malwarebytes cloud, data is preserved for 24 hours and then submitted to RocketCyber syslog collector when communication is established. Any data older than 24 hours will not be submitted to the RocketCyber syslog collector.
- Next, see Configuring the RocketCyber Syslog Collector if this step has not been performed.
Congratulations, your RocketCyber SOC is now prepared to receive Malwarebytes threat data.