Configuring the RocketCyber Syslog Collector
This article describes how to configure the Syslog Collector. The Syslog Collector is designed to aggregate threat events from third‑party vendors when the RocketCyber SOC platform does not have an existing purpose‑built integration for that vendor.
Common Event Format (CEF) and Log Extended Event Format (LEEF) are open standard Syslog formats adopted across numerous application, cloud, and hardware vendors for log management and security information interoperability.
The Syslog Collector works specifically with vendors that support Syslog CEF and LEEF log formats.
Configure the Syslog Collector
The Syslog Collector is not enabled from the App Store by default. Contact RocketCyber Support to have the Syslog Collector enabled for your organization.
Once enabled:
1. Go in context as the tenant where data will be aggregated.
-
The Syslog Collector is configured at the organization level.
2. Click Configure to open the configuration settings.
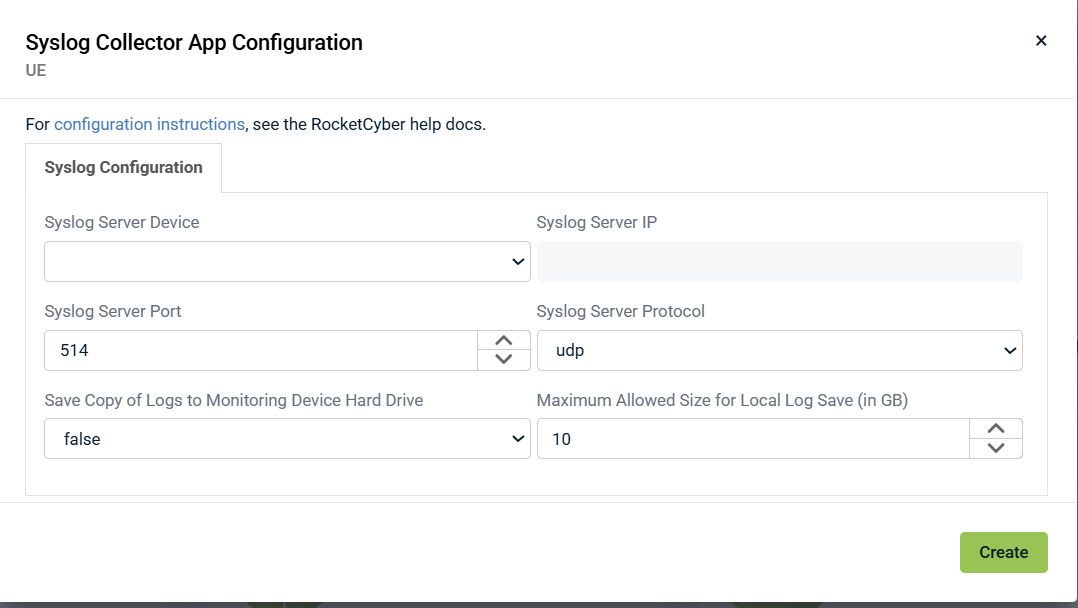
3. Select a device from the drop‑down menu and click Create.
-
A Rocketagent must already be deployed to a Windows device prior to configuration.
Recommendations
- UDP Port: The default configuration uses UDP 514. If this port is already in use on the selected device, change it to an unused port such as 541 or 551.
- IP Address: When selecting the device for Syslog ingestion, it is recommended to change the IP configuration from DHCP to a static IP address.
- Device selection: Ensure inbound UDP traffic is permitted on the selected device and not blocked by firewall rules. An always‑on device is recommended.